IPAM stands for IP address management. It allows you to assign and manage IP address for VPC across your AWS environment. It can assign IP address to different accounts and regions which are part of your organization. It will help us to manage the IP ranges so that it will not override with other VPCs or with on-premises ranges.
- Organize IP address space into routing and security domains
- Monitor IP address space that’s in use and monitor resources that are using space against business rules
- View the history of IP address assignments in your organization
- Automatically allocate CIDRs to VPCs using specific business rules
- Troubleshoot network connectivity issues
- Enable cross-region and cross-account sharing of your Bring Your Own IP (BYOIP) addresses
- Provision Amazon-provided contiguous IPv6 CIDR blocks to pools for VPC creation
Architecture to follow
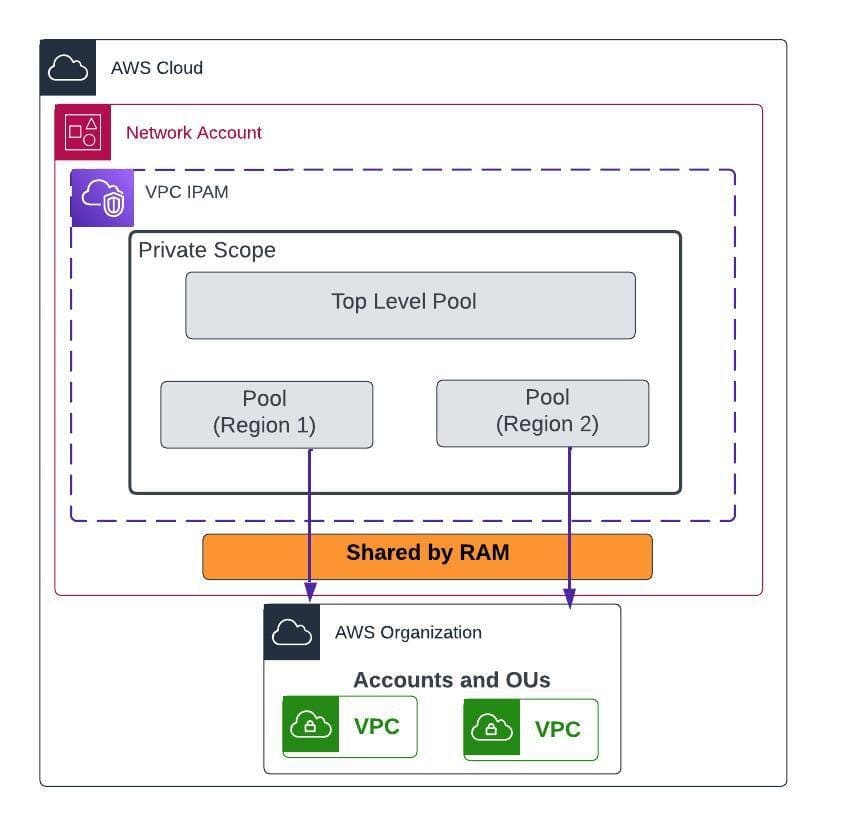
IPAM Pool hierarchy for multiple AWS regions and also share to whole organization using RAM.
Scope: There are 2 scopes for IPAM. Private scope for private IP address management. Public Scope for public IP address management.
Pool: It is a CIDR range. IPAM pools enable you to organize your IP addresses according to your routing and security needs. You can have multiple pools within a top-level pool.
Allocation: A assignment to a VPC or a resource. You manage and monitor the allocation in the IPAM dashboard.
How it works?
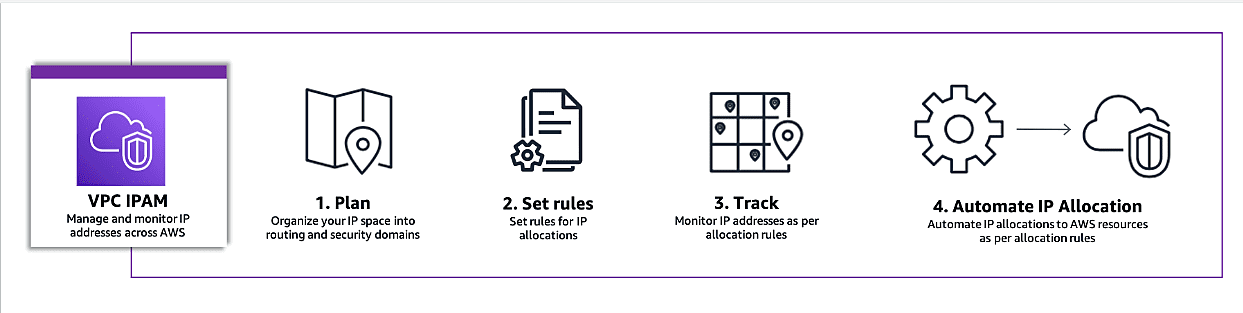
- Organize your IP address space into routing & security domains
- Set rules for IP allocation
- Share the IPAM pools with other accounts via RAM
- Monitor IP address across organization
- Automate IP allocation to AWS resources as per allocation rules
Pre-requisite
- An AWS Account
- AWS organization with multiple Accounts. (optional)(Practical scenario)
Steps to Follow
You can use IPAM to monitor IP space across your entire Amazon Web Services Organization, or for a single account. Configure your settings to get started, and then create an IPAM.
- Delegated administrator
- Create the IPAM
- Create Parent pool and child pools
- Create RAM to share the pools to organization
- Create a VPC with shared IPAM pools
Delegated Administrator
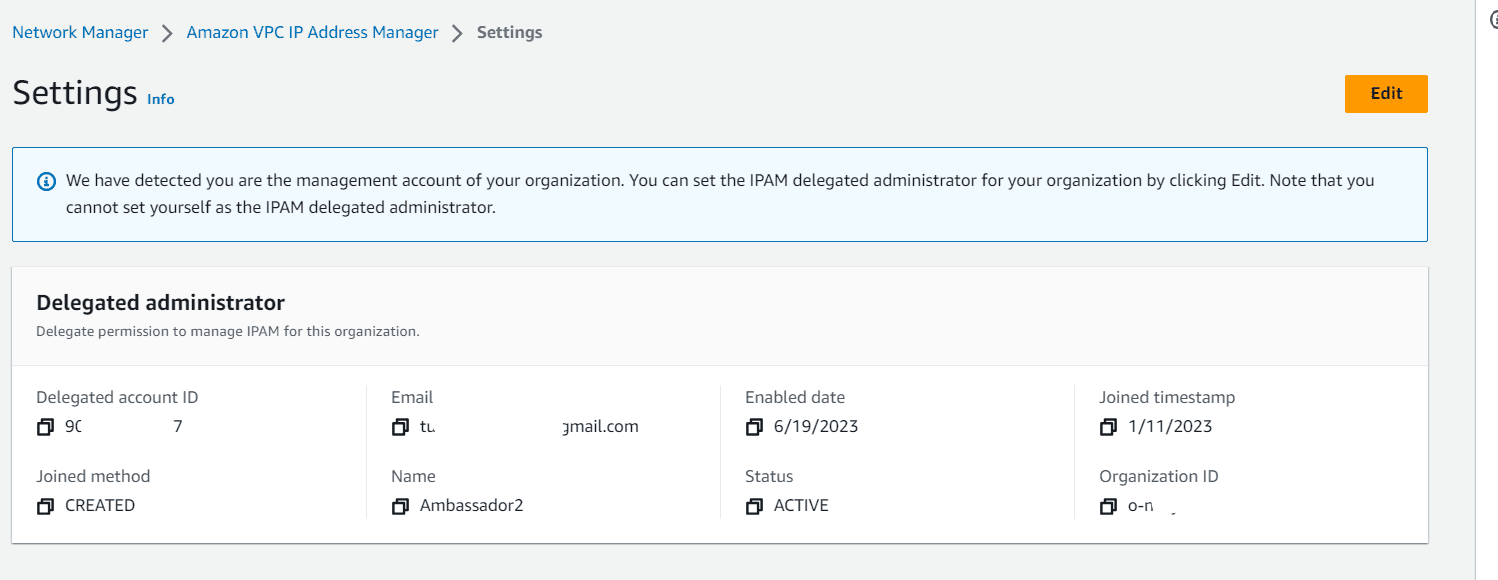
Login to AWS Management Account and navigate to AWS Network Manager. Under IP management, click on Organization settings.
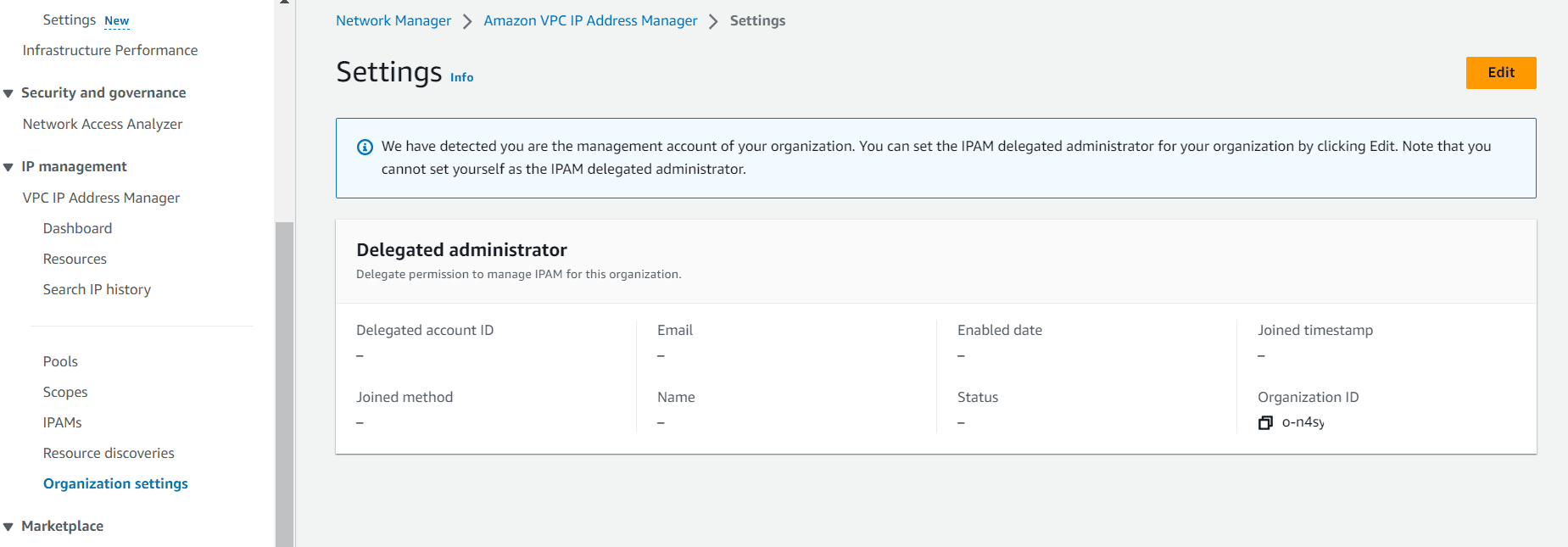
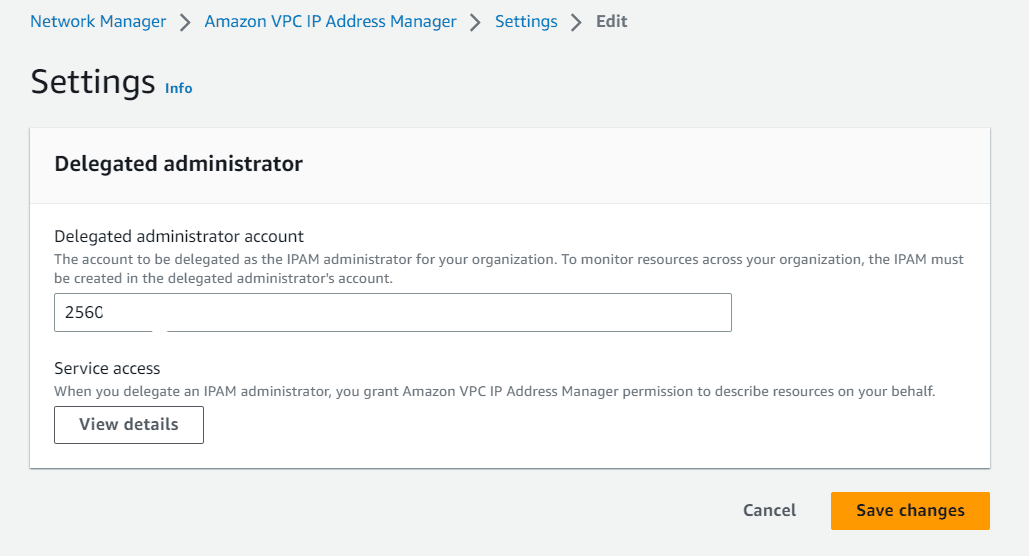
Click on edit, mention the Account number which is going to act as a delegated admin account for IPAM. Mostly the Network Account
Create IPAM
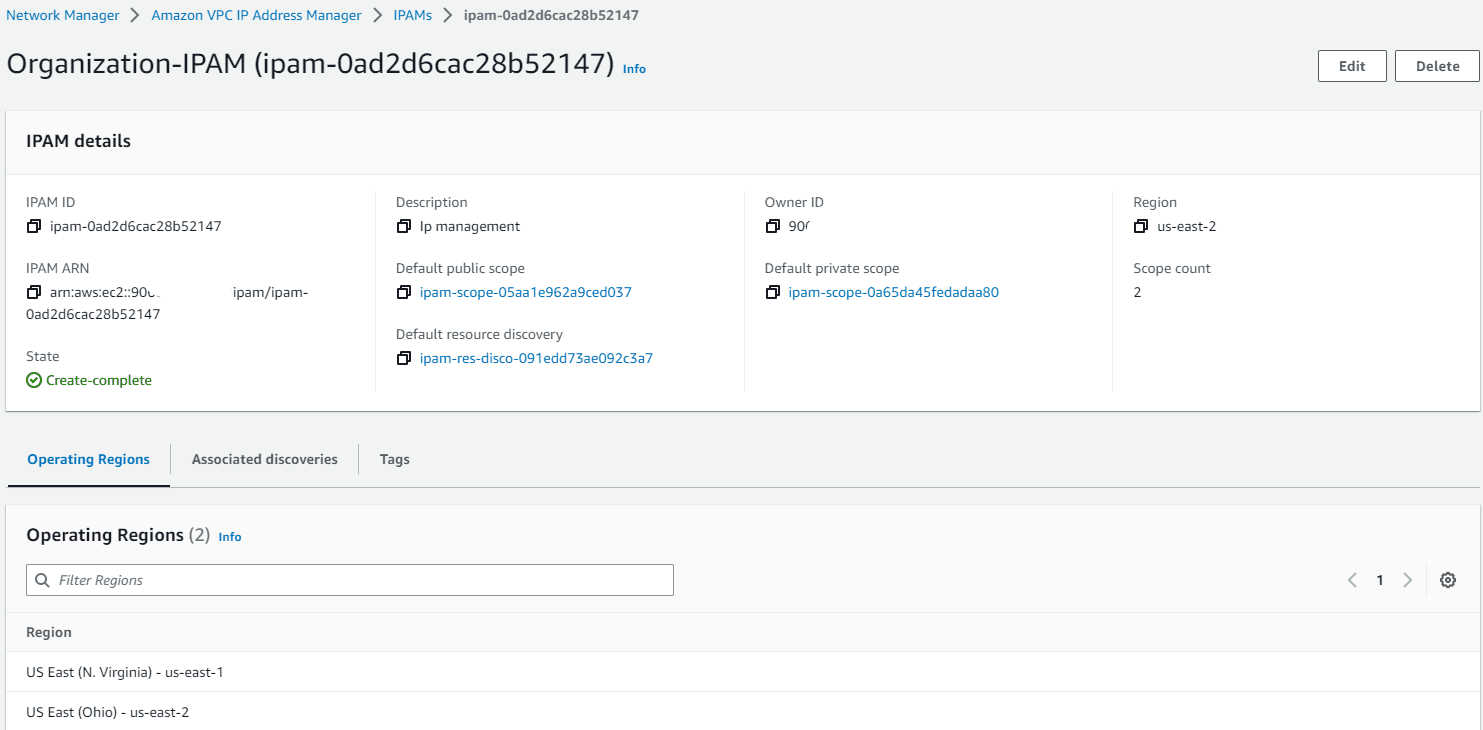
Login to delegated IPAM Account, navigate to AWS Network Manager and under IP management, click create IPAM
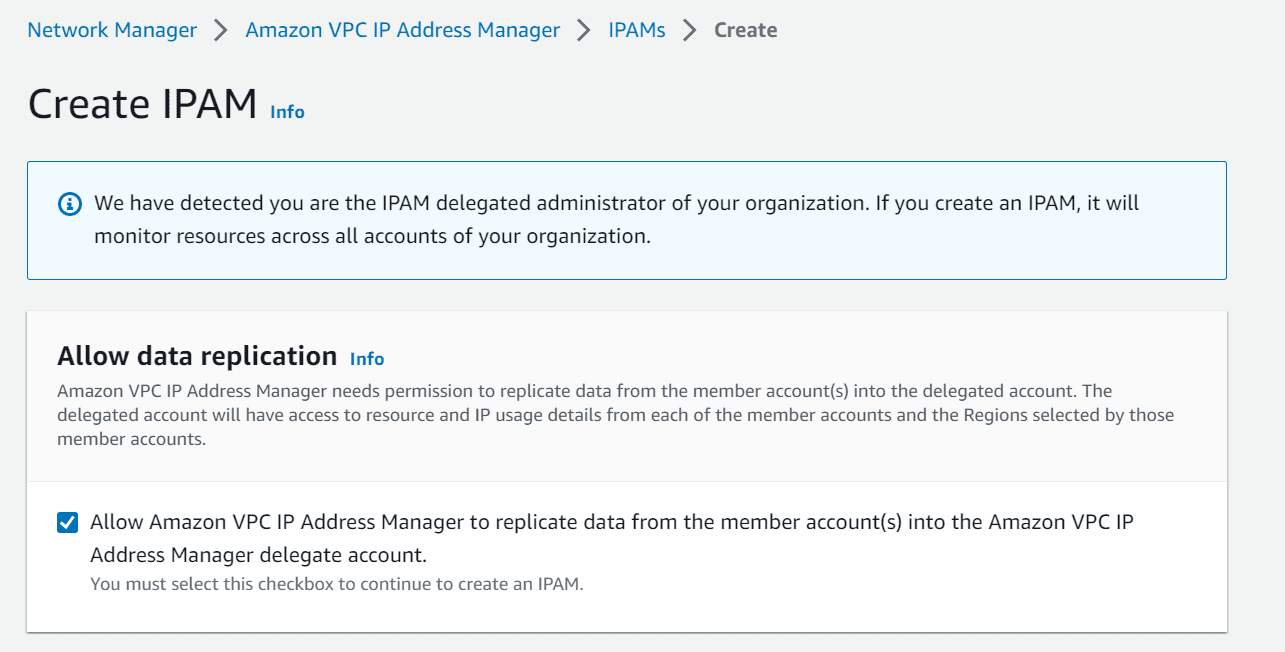
Tick the checkbox to allow AWS IPAM to replicate data from member account to delegated admin account.
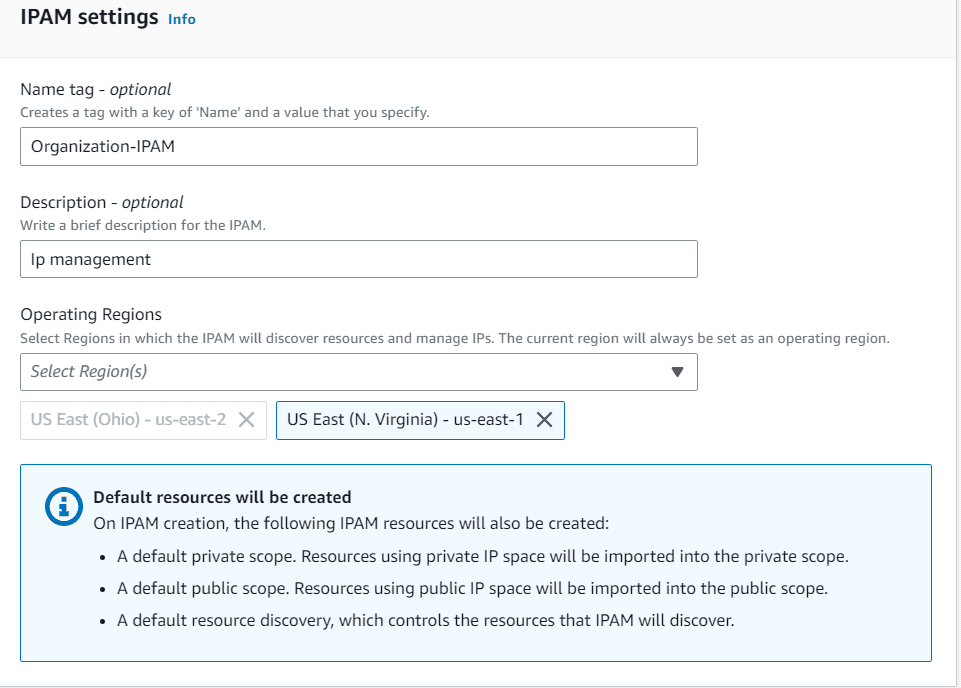
Fill the Name and choose the region in which you wanted to deploy IPAM feature and click on create.
Create Parent Pool and Child pools
Click on pools, create pool. Choose the scope as private and create a parent pool with no locale.
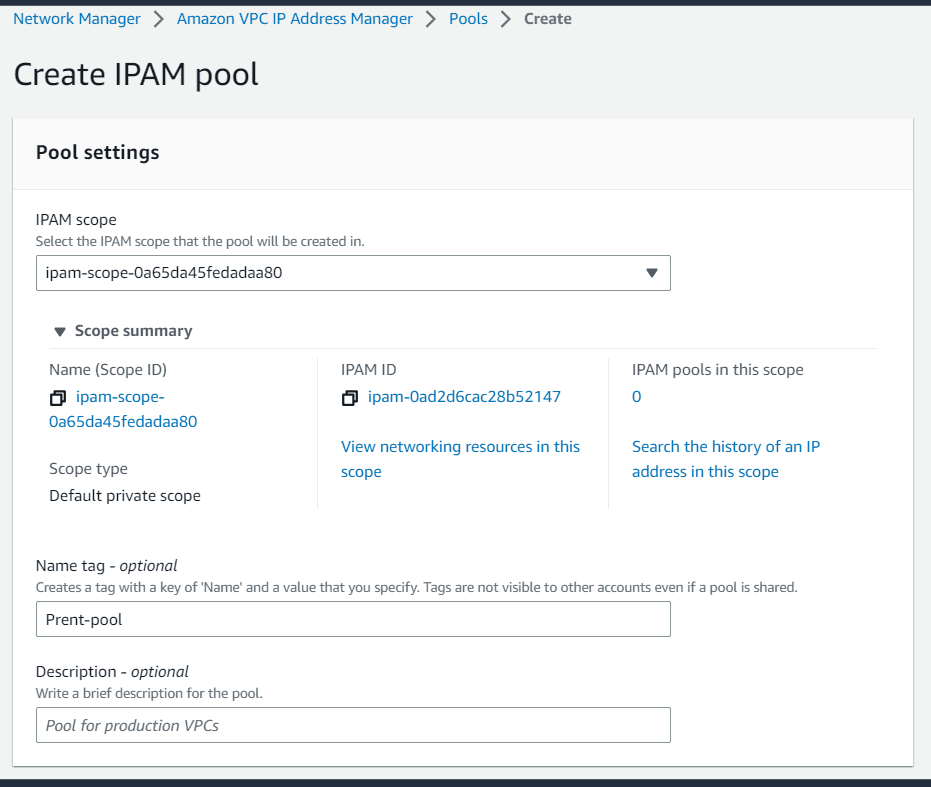
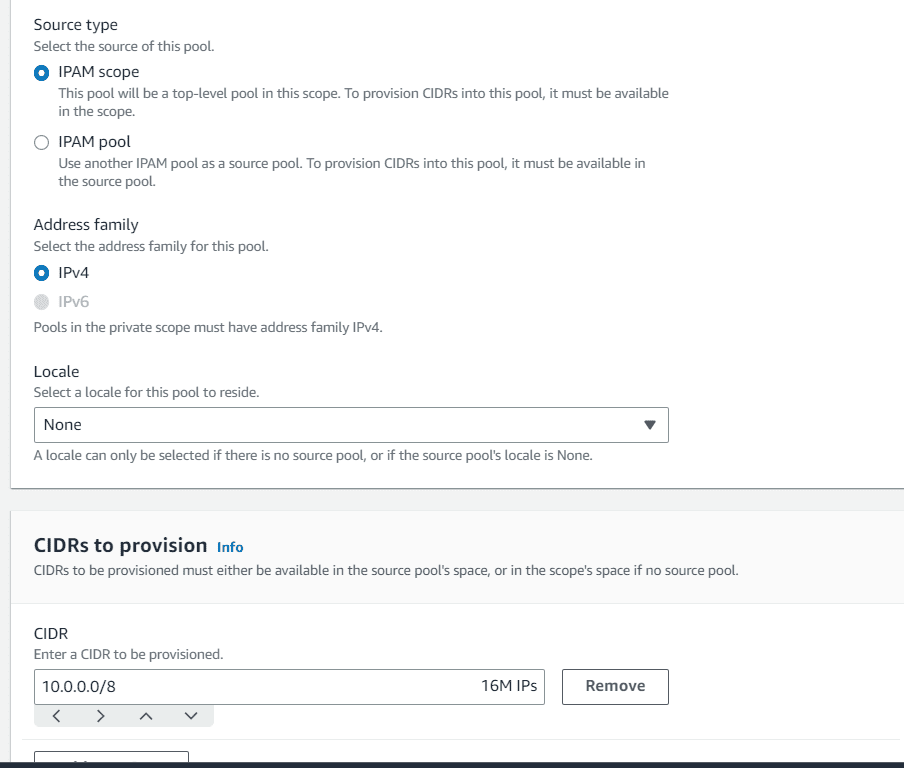
Choose the pool hierarchy as IPAM scope and add a CIDR range for parent pool
The parent pool will be created. There are multiple options under pool.
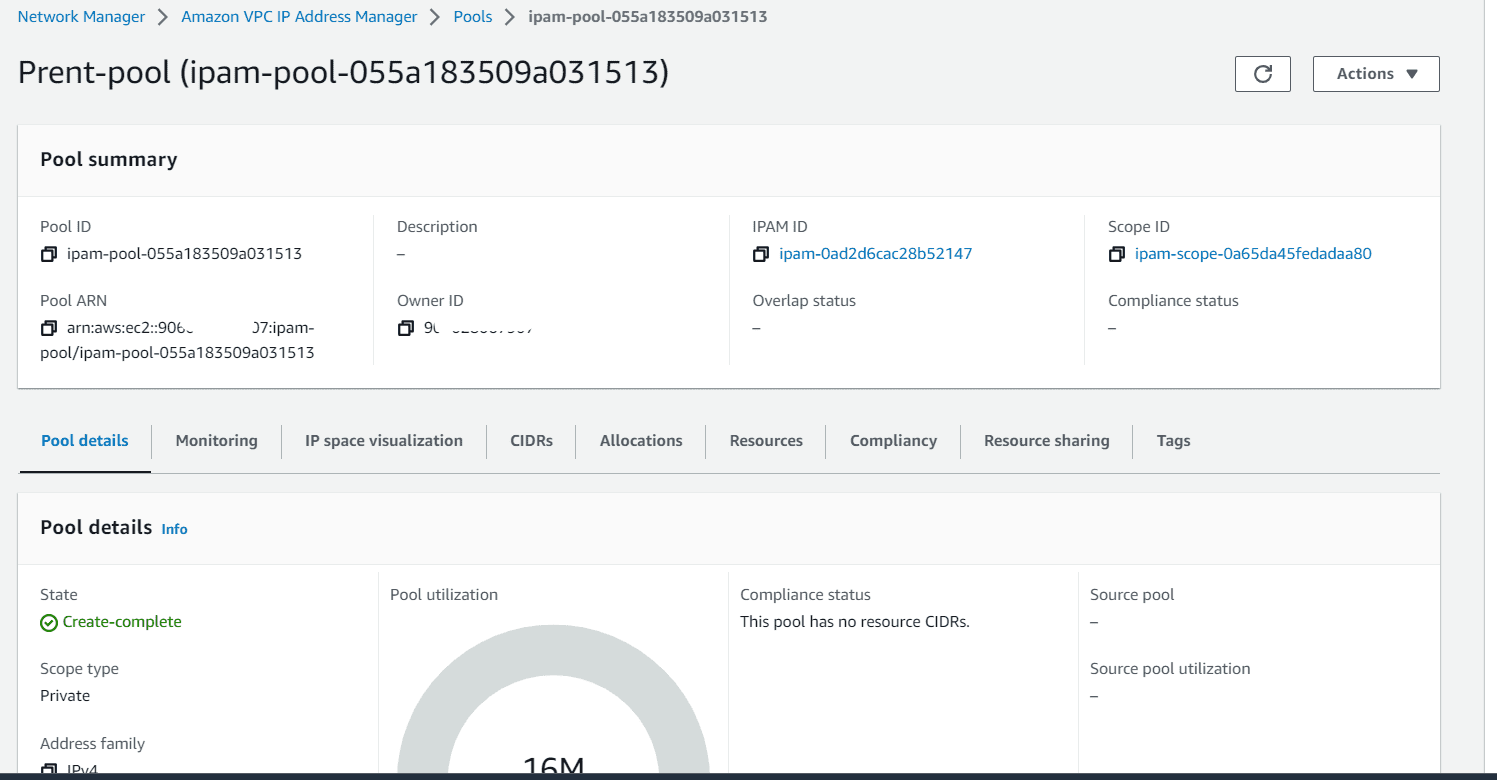
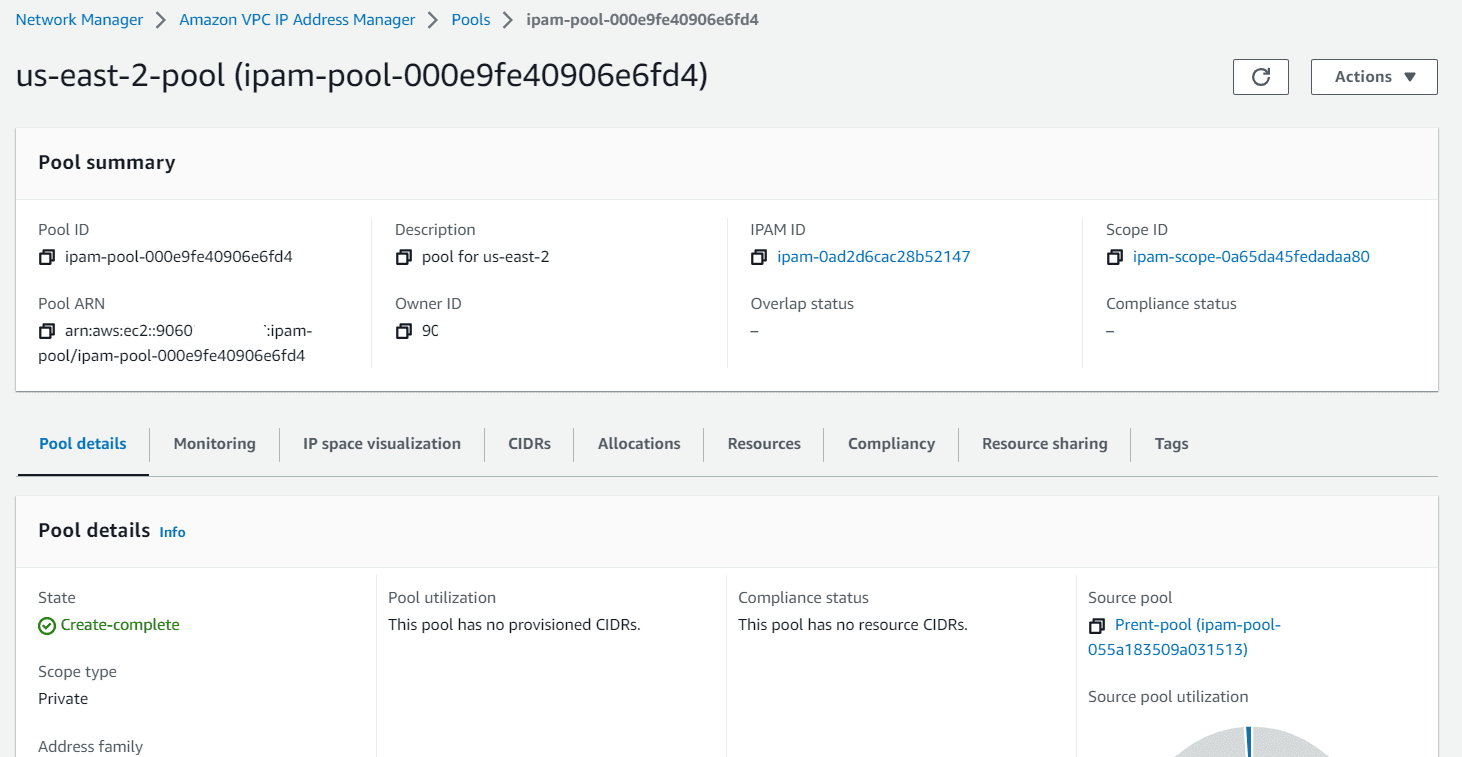
Create pools for us-east-1 region and us-east-2 region
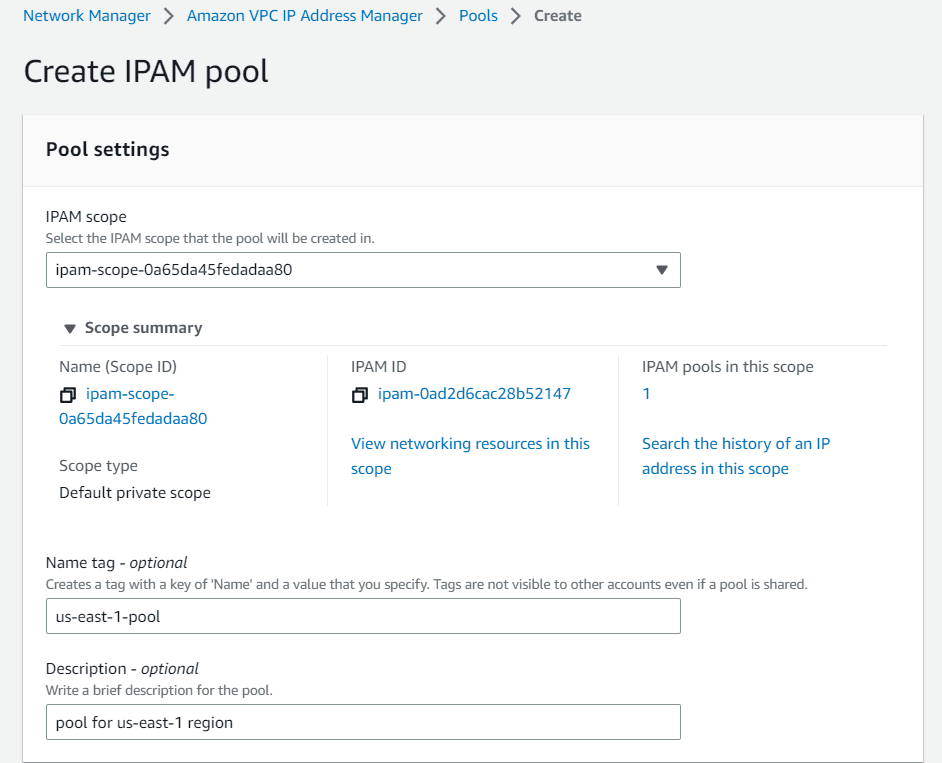
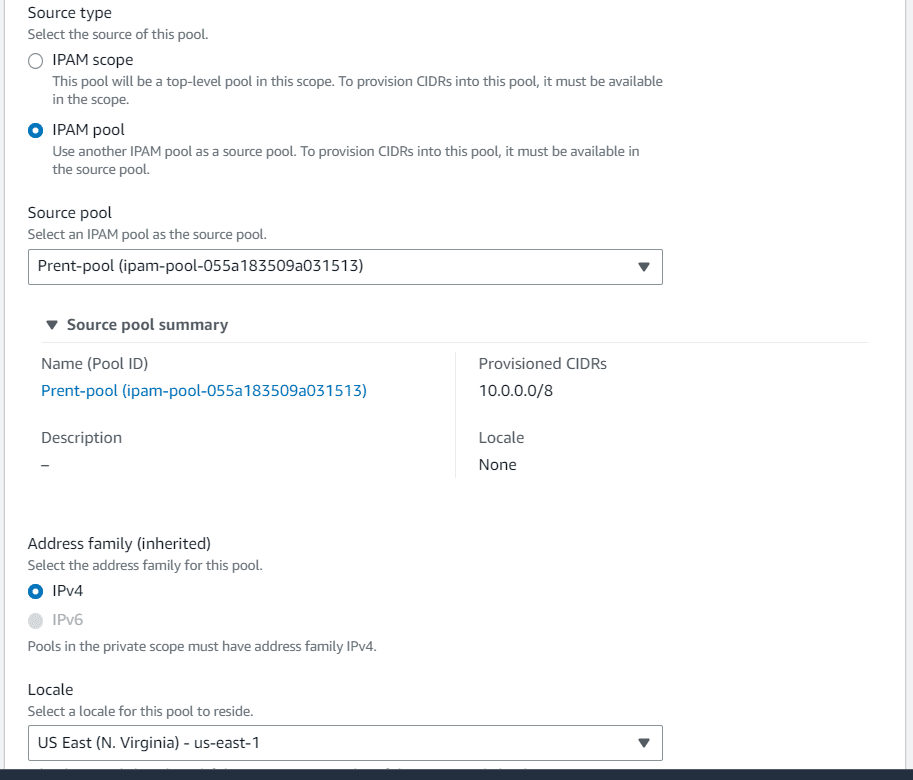
In the pool hierarchy choose IPAM pool as source type, choose parent pool as source pool from drop down.
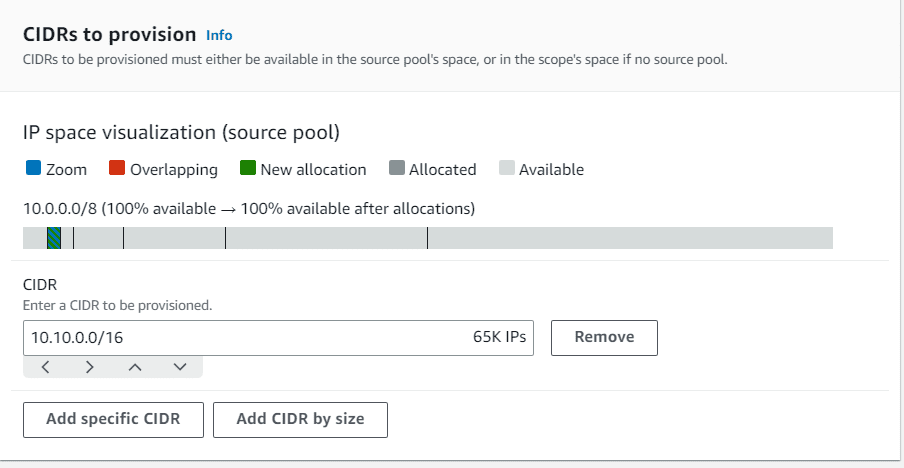
Select locale as us-east-1, 10.10.0.0/16 as CIDR to provision.
Click on Allocation rule settings, choose allow automatic import, choose Netmask compliance as per your organization need.
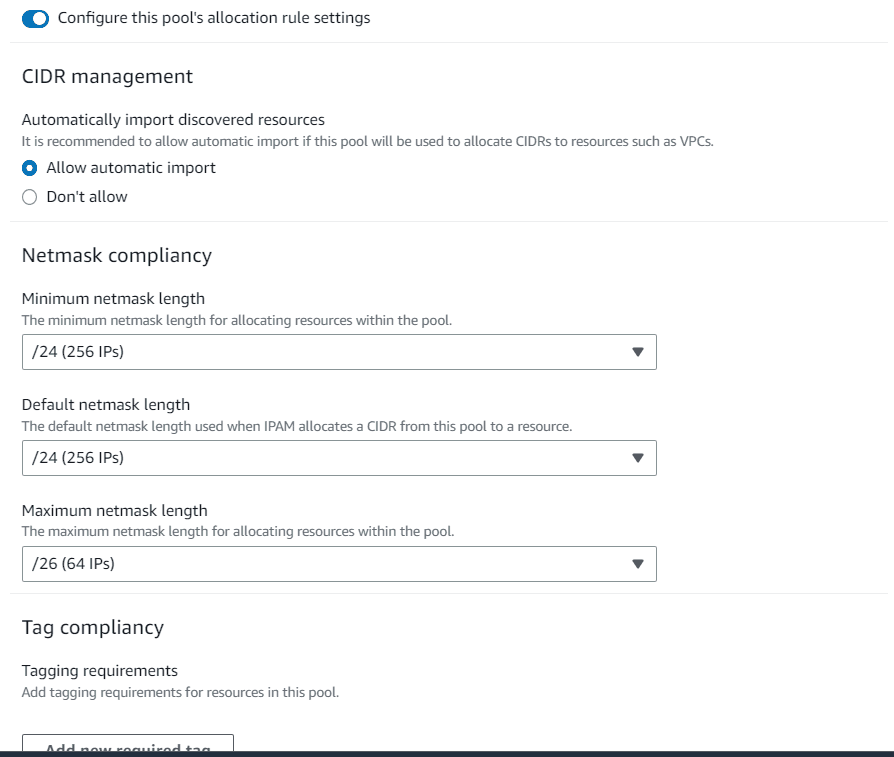
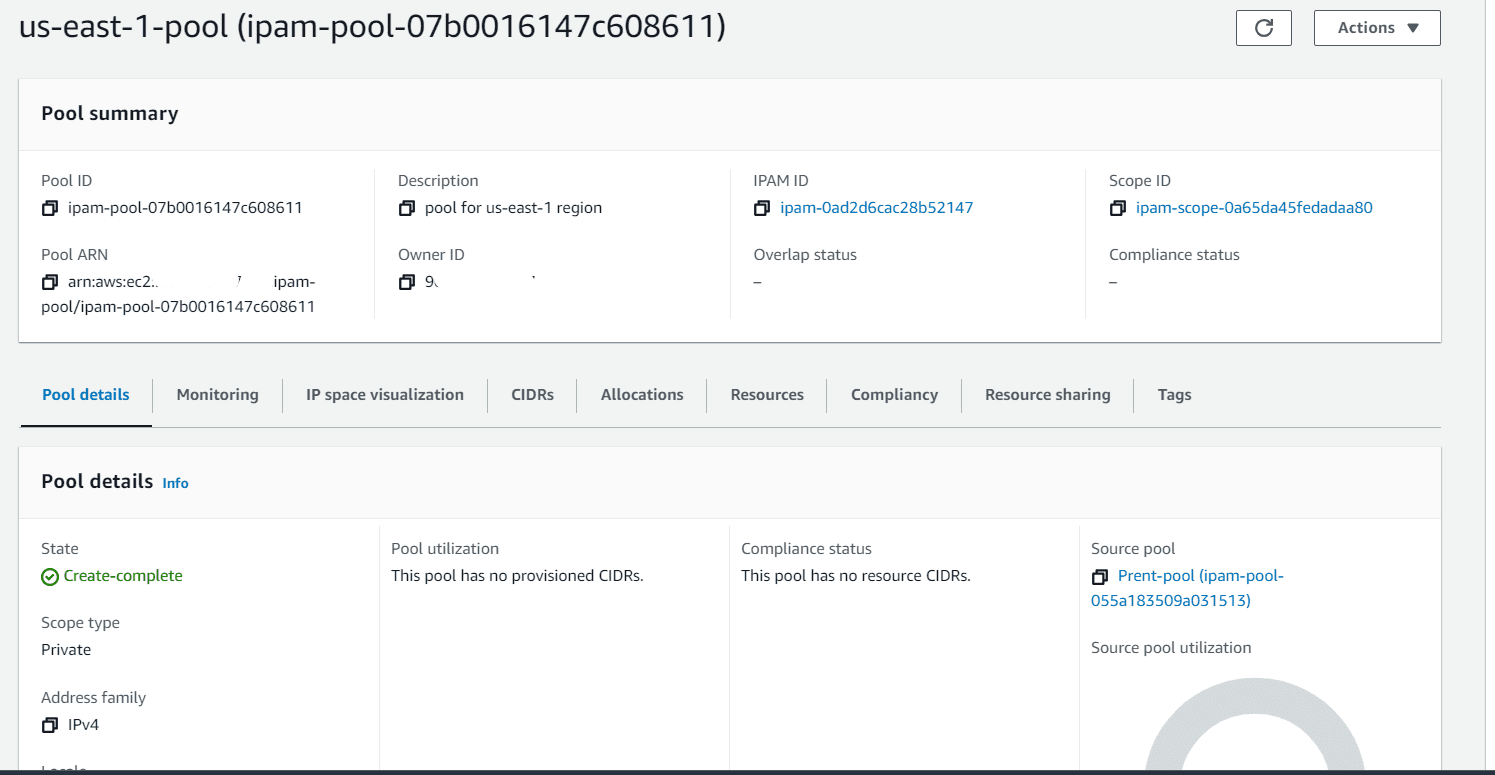
Create the pool for us-east-2 with same configuration and choose a different CIDR range.
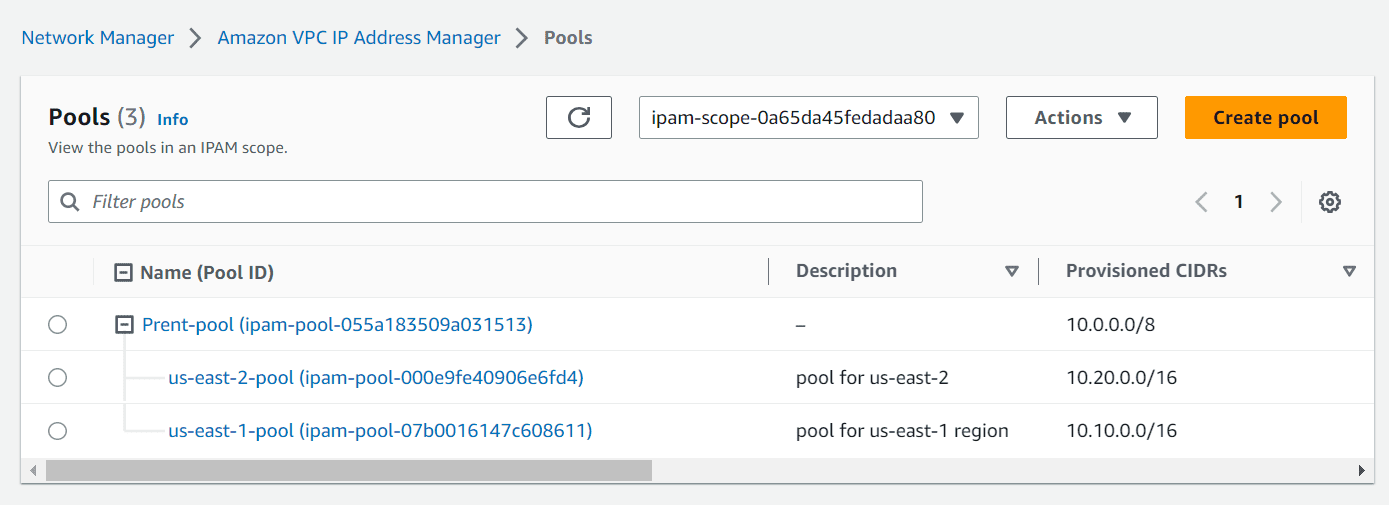
Your IPAM pool should look like below
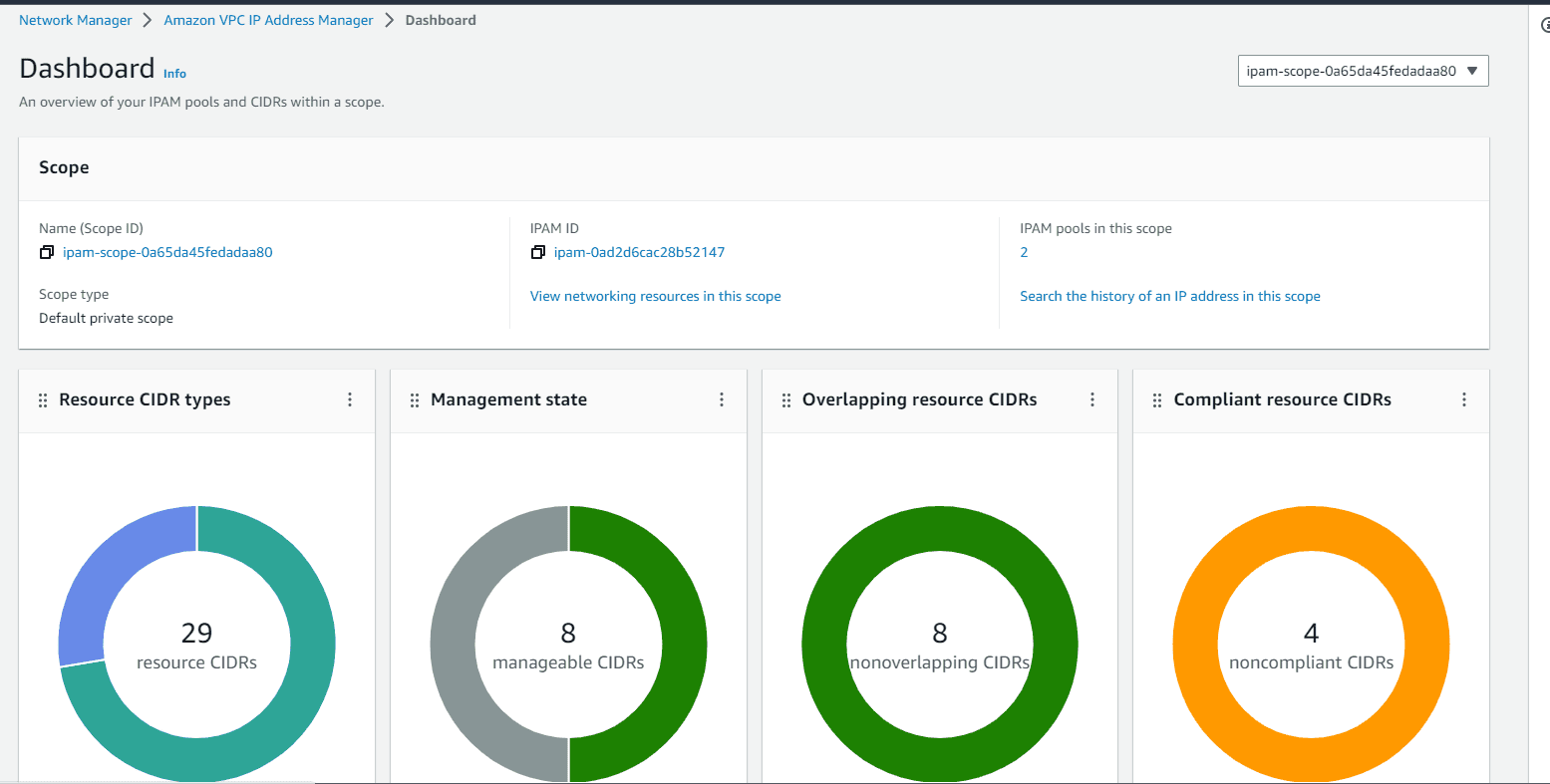
The dashboard looks like below, as we choose import all existing CIDR while pool creating. All existing VPC CIDRs are now part of the managed IPAM.
Create RAM to share the pools to organization
Now let’s share the resource to the whole organization. Click on resource sharing under ipam-pool.
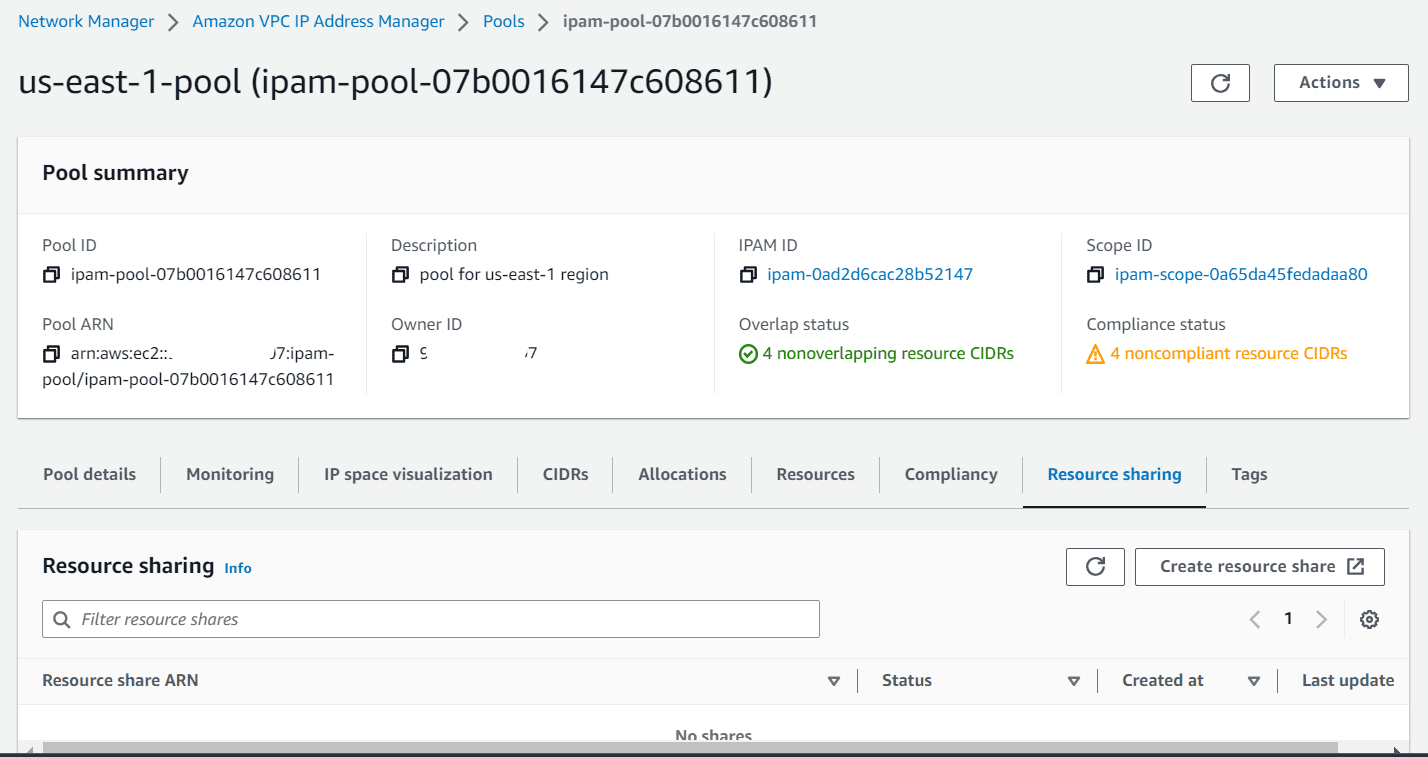
Click on create resource sharing, it will take you to RAM page.
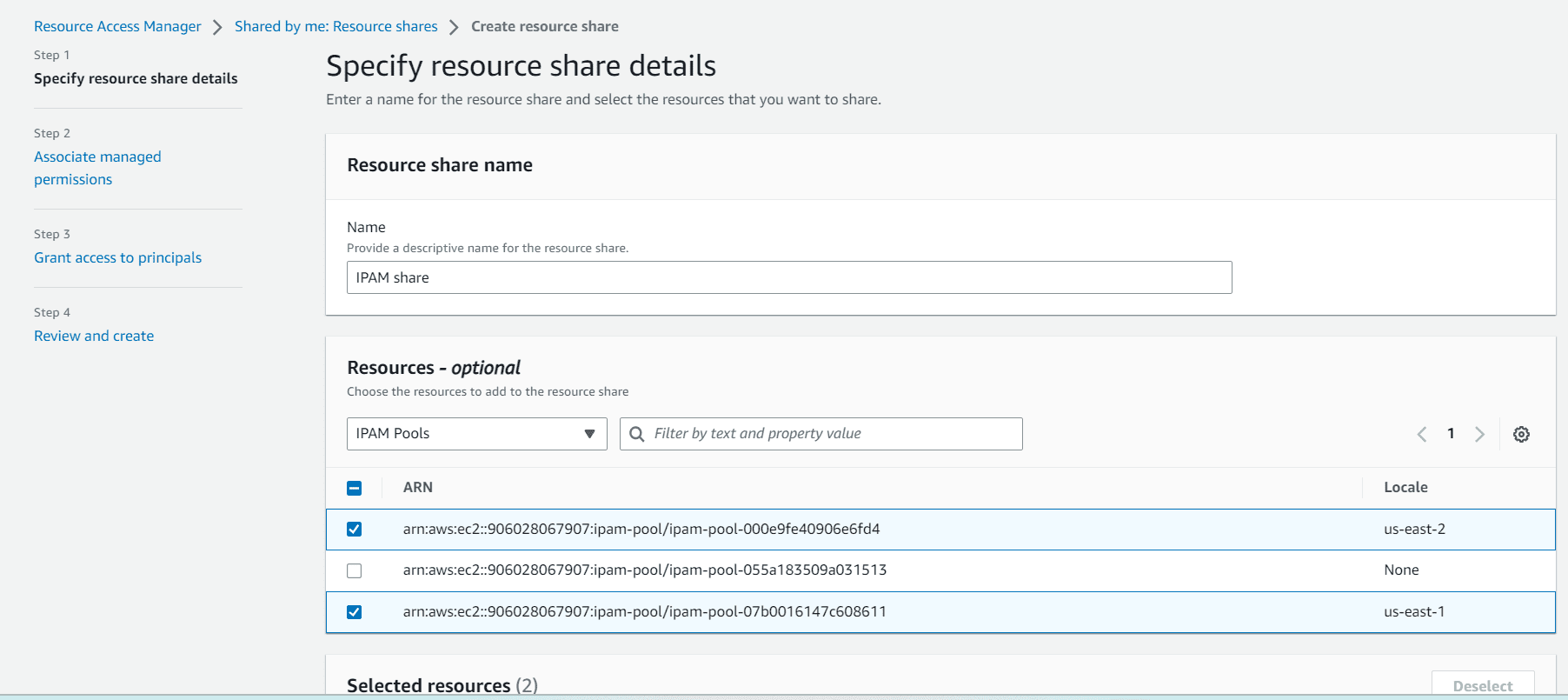
Provide a name, in resources section choose IPAM pools and chose the pools from the dropdown list. Click next
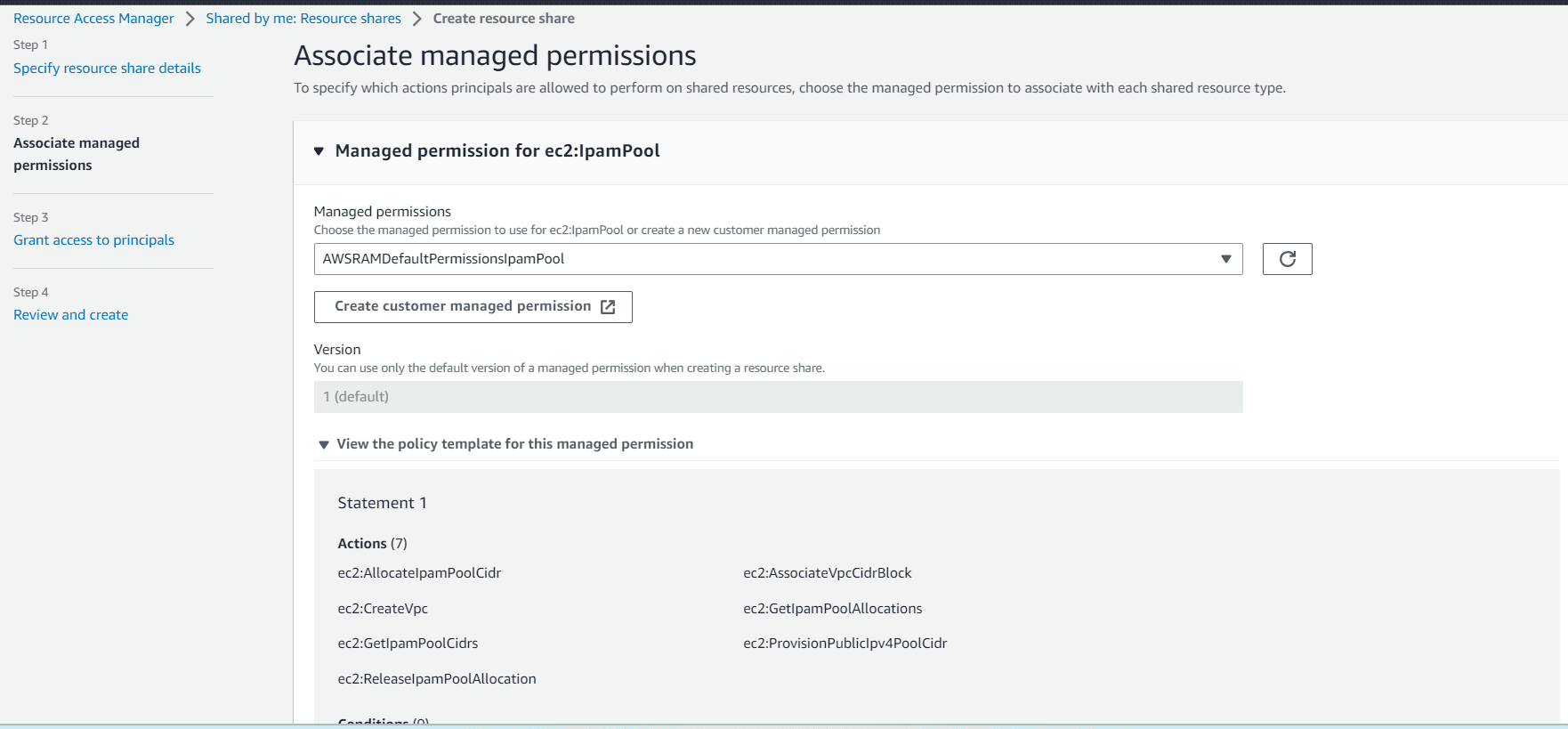
Then click on allow sharing only within your organization, select principal type Organization and enter the organization ID.
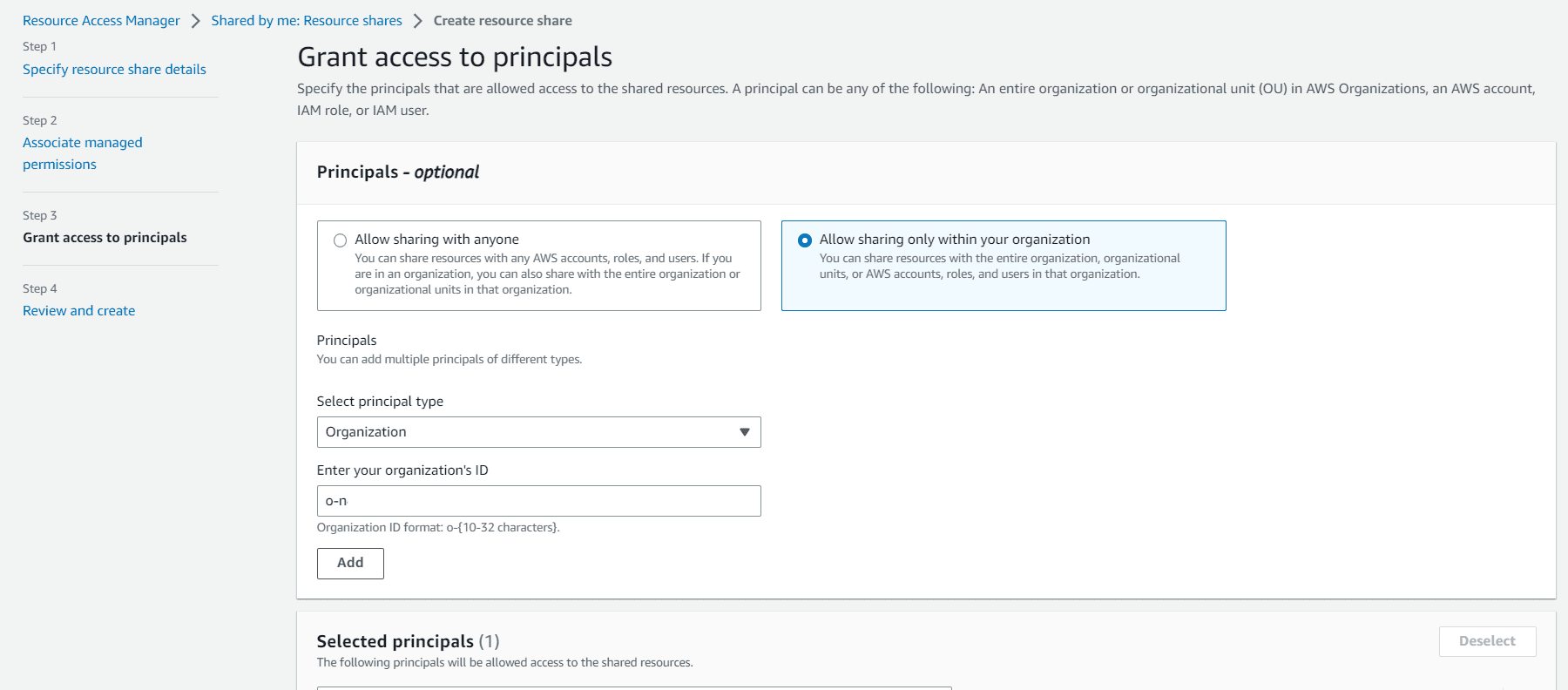
Click on next, after reviewing create resource sharing
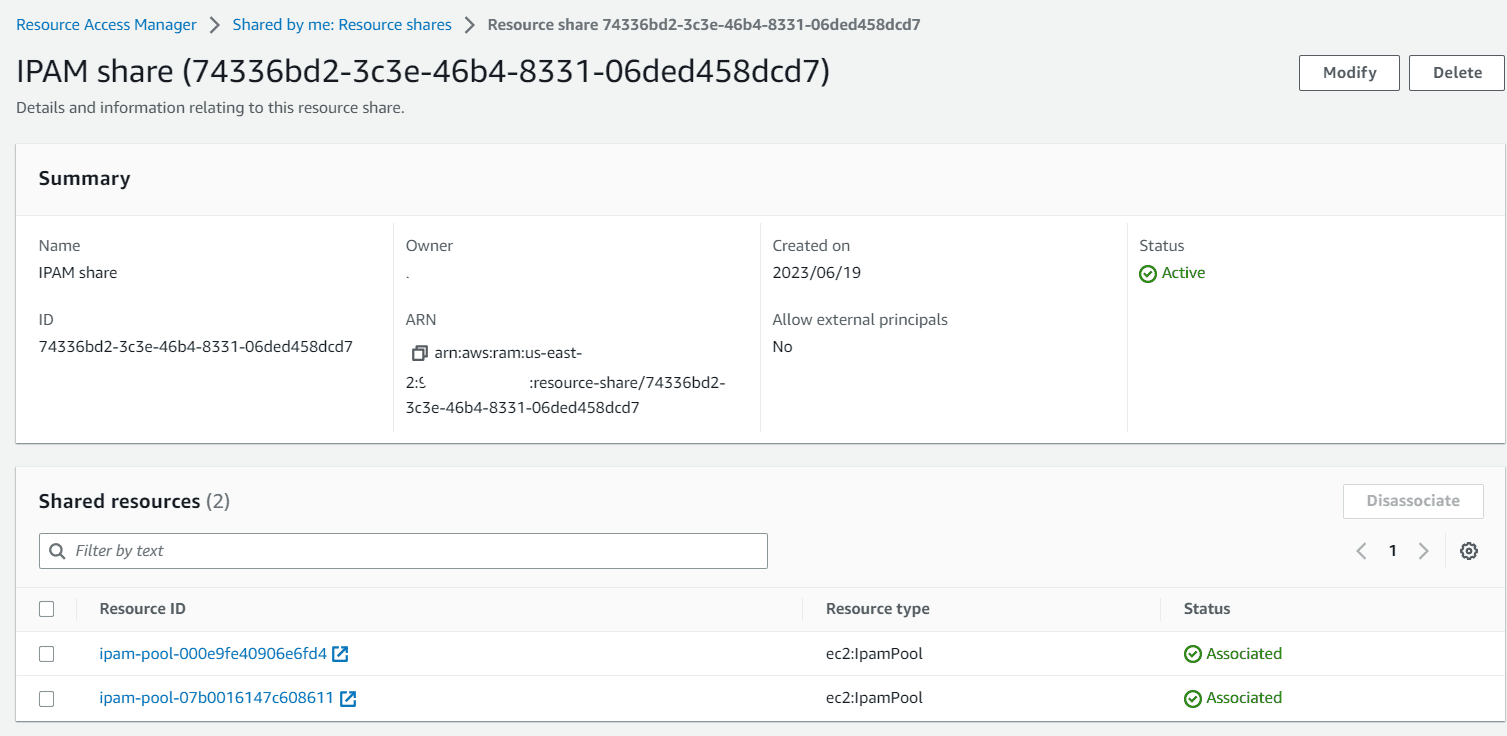
Both pools are now shared with the organization.
Create a VPC with shared IPAM pools
Navigate to VPC and click on create VPC
Provide a name, in IPv4 CIDR block choose IPAM-allocated IPv4 CIDR block
Select the us-east-2 IPAM pool from the dropdown and the other will greyed out.
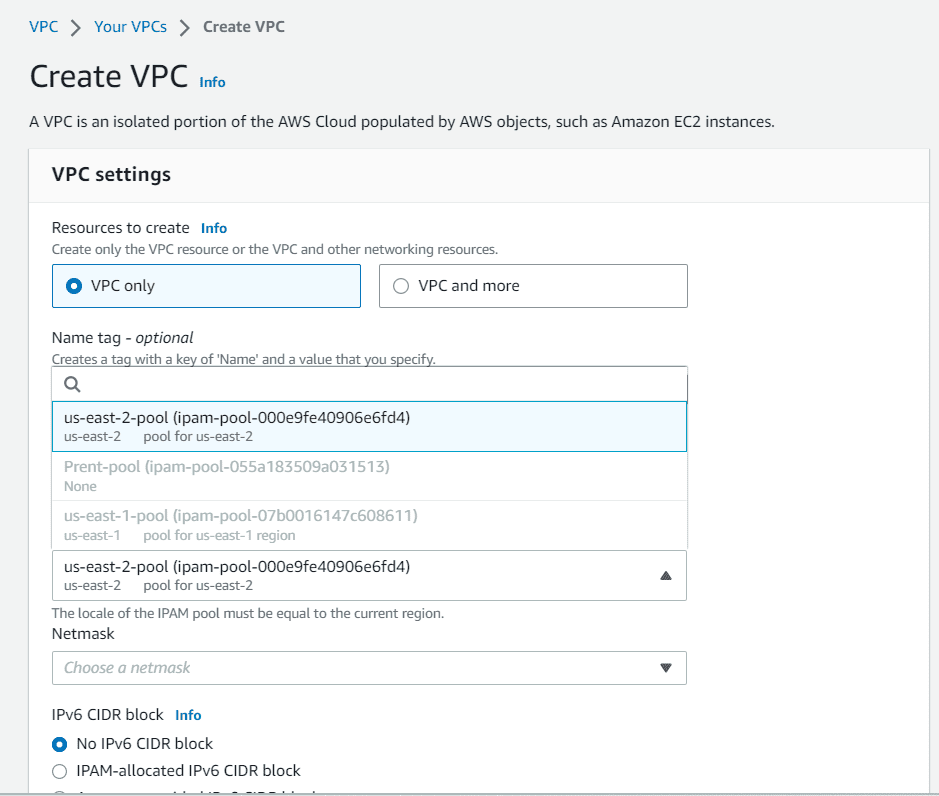
Choose a netmask and click on create
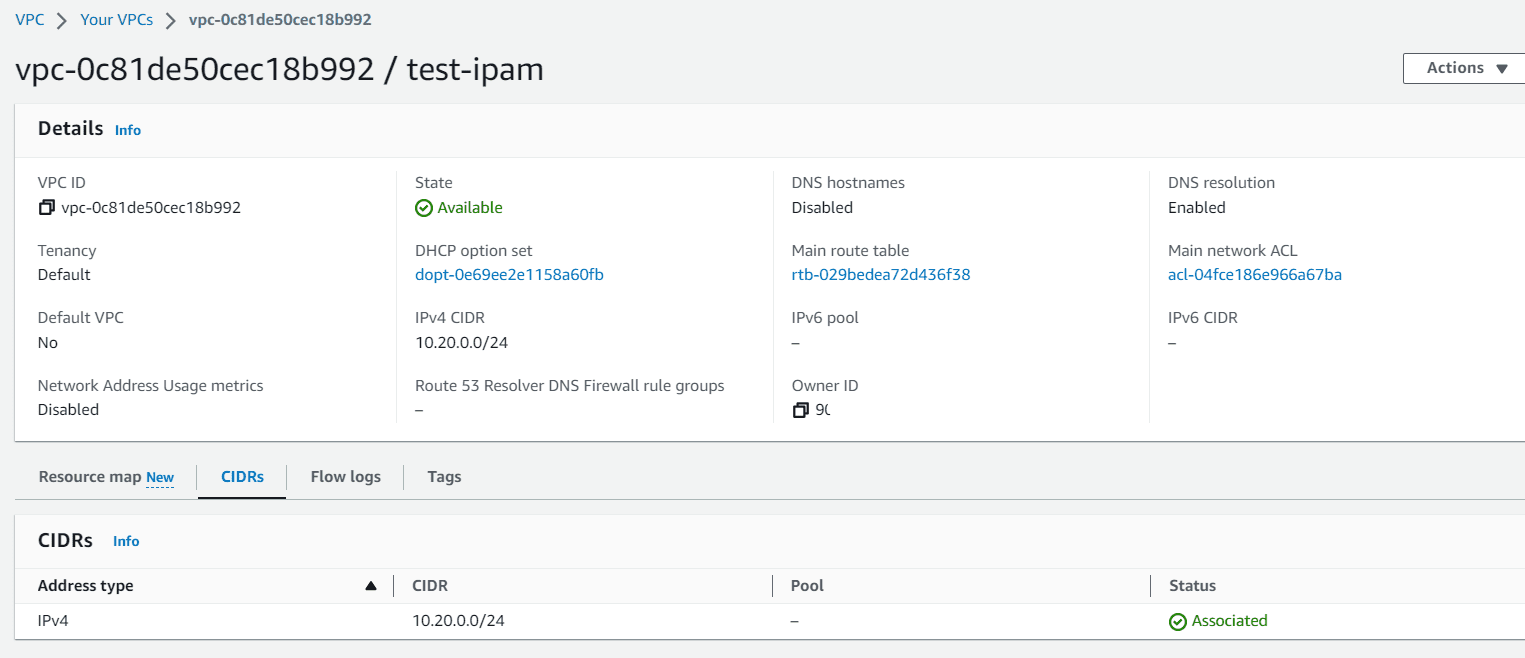
Let’s go back to IPAM dashboard, click on us-east-2 pool
Under allocation section the newly created VPC will available.
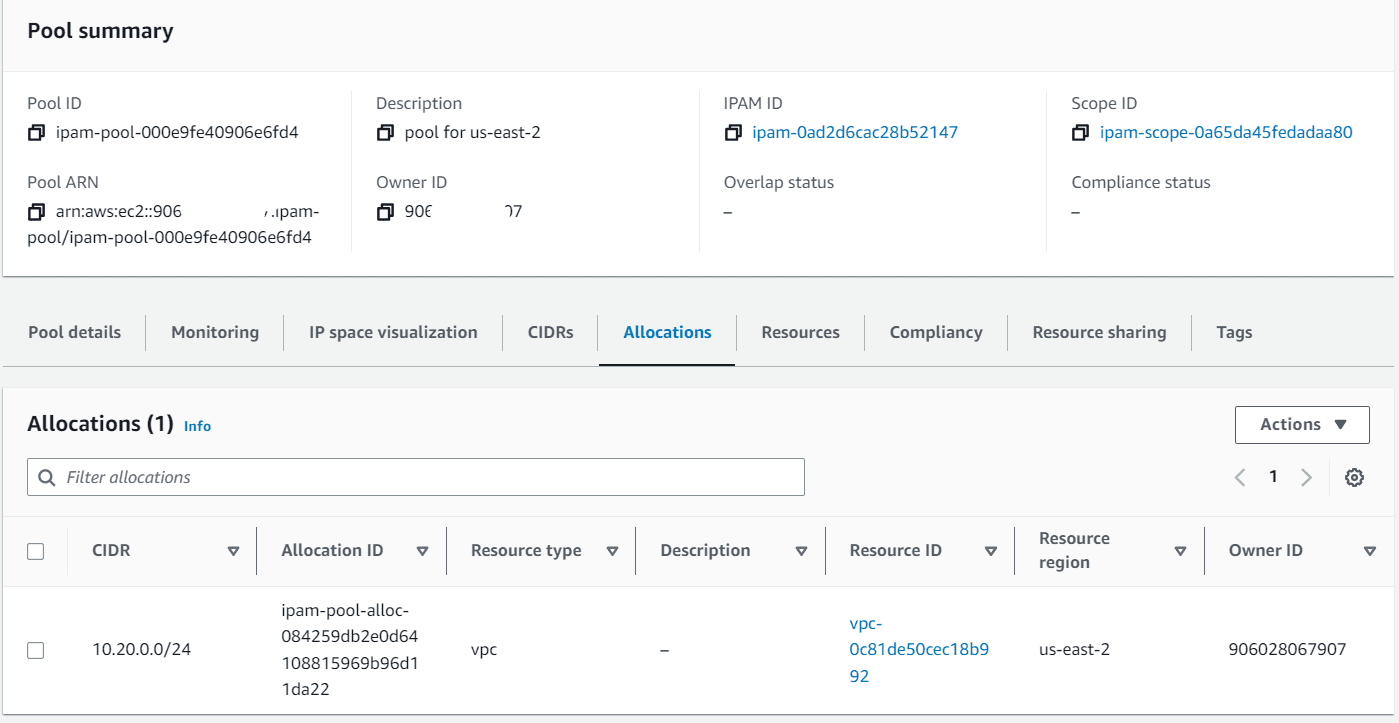
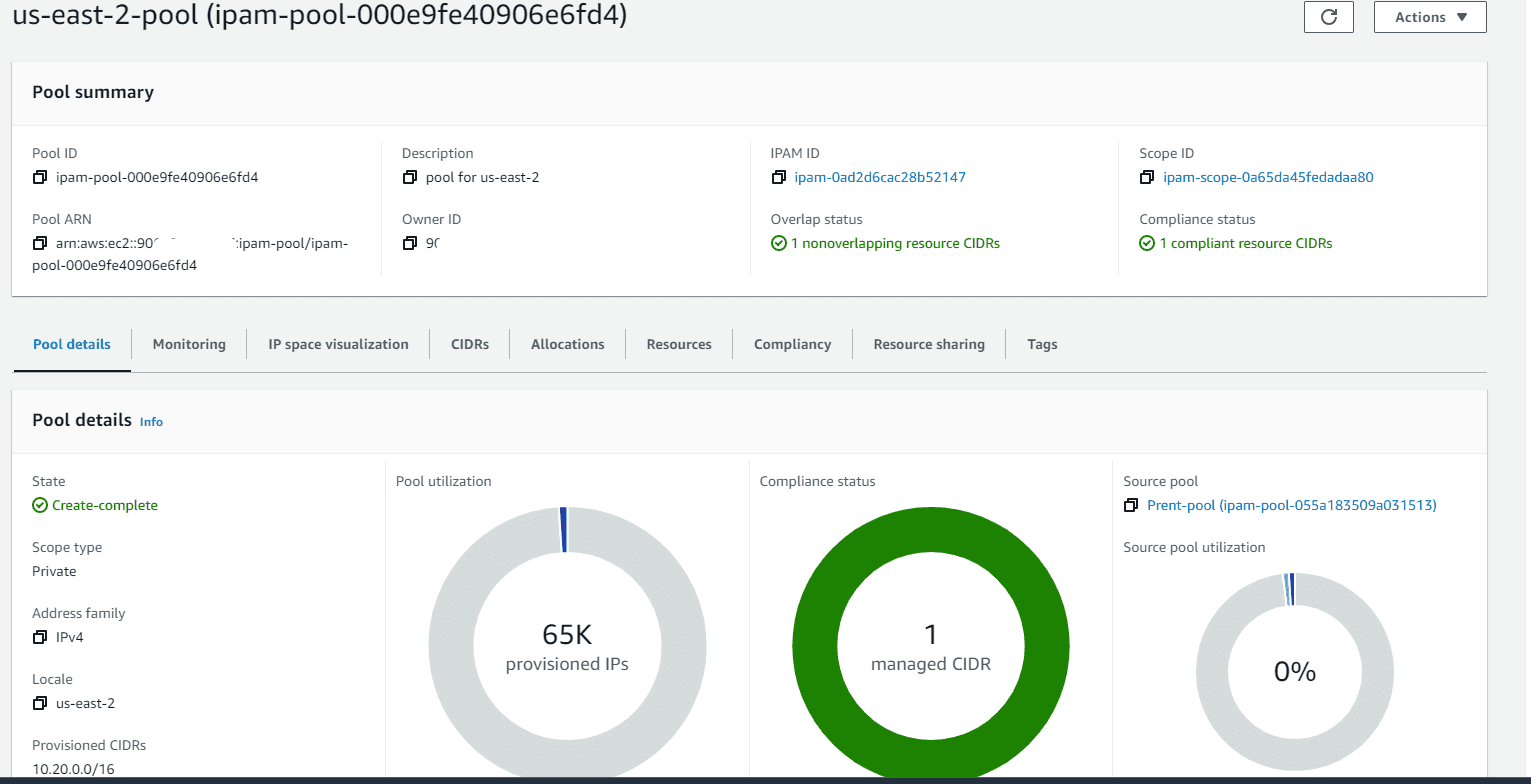
The IPAM will also show non-compliant, if any VPC created outside of the IPAM pool range is allocated to the region.
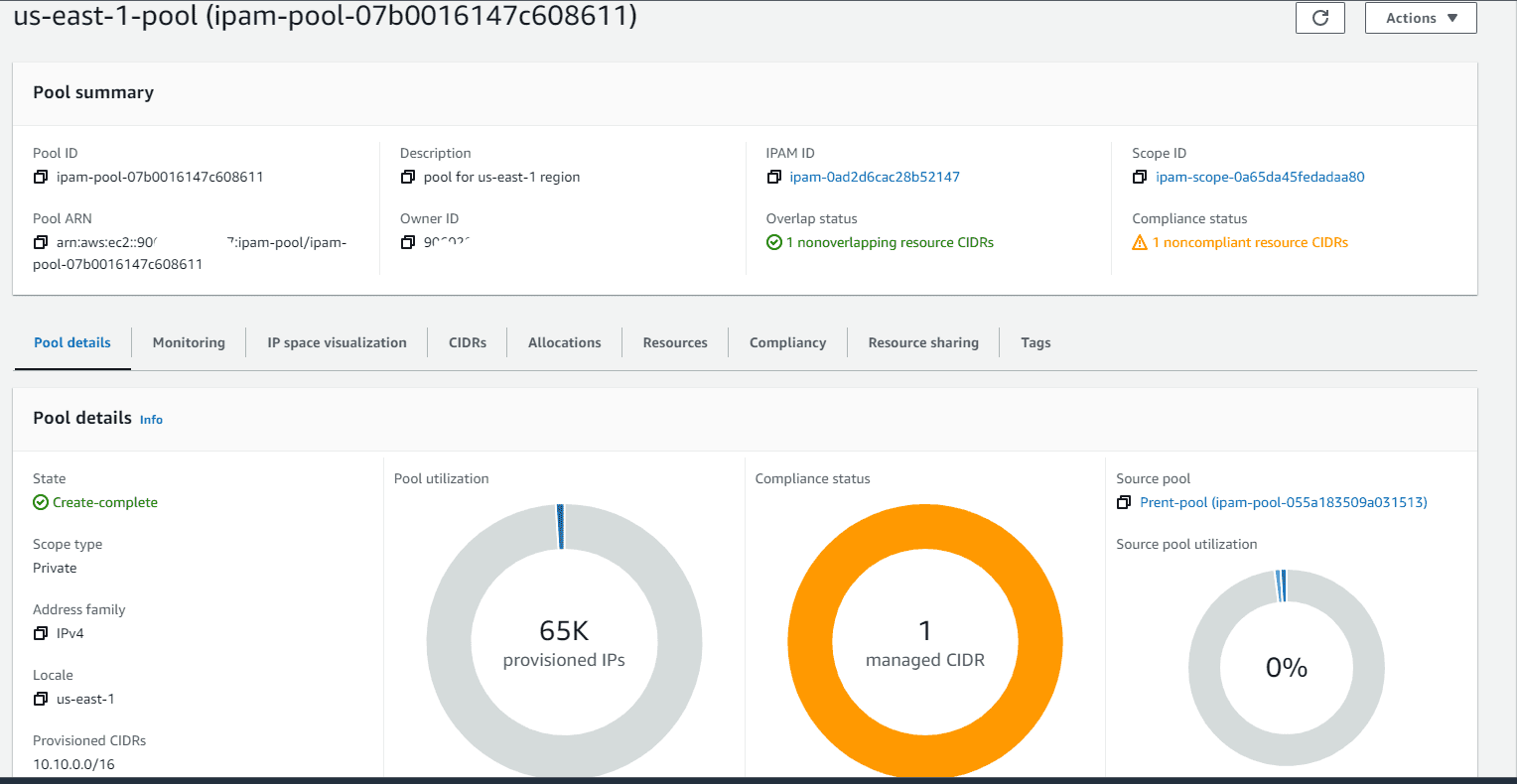
Intentionally I created 1 VPC in us-east-2 from us-east-1 pool range manually. Now it’s showing non-compliant under us-east-1 pool.
Conclusion
AWS IPAM is an IP address management and monitoring feature which helps organizing the IP address allocation and CIDR provisioning in VPCs. So there will be no over-lapping of IP address space.
Read More:
AWS for Beginners: Overview of AWS IAM Access Analyzer: Part 53
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.



Leave A Comment