Introduction
In this blog, we are going to describe details on domain-wide security settings on GSuite to help any GSuite mail administrator to protect his users against phishing attacks, and to strengthen his domain security posture at best. Google Admin security settings have many components to configure to enable his domain mail server to safeguard against any such vulnerabilities.
Components of Google Admin Security settings
Google Admin Security constitutes the below components to provide information about the default settings available and enable the administrator user to configure those settings to improve his domain security and construct a plan against phishing attacks & malicious email receiving. Also improves domain user’s access with third-party applications securely.
- Alert Center
- Security rules
- Password Management
- Less secure apps
- 2 Steps verification
- Account recovery
- Login challenges
- Setup SSO for SAML applications
- Setup SSO with a third-party IdP
- Advanced Protection Program
- Context-aware access
- Google cloud session control
- Advanced settings App access control
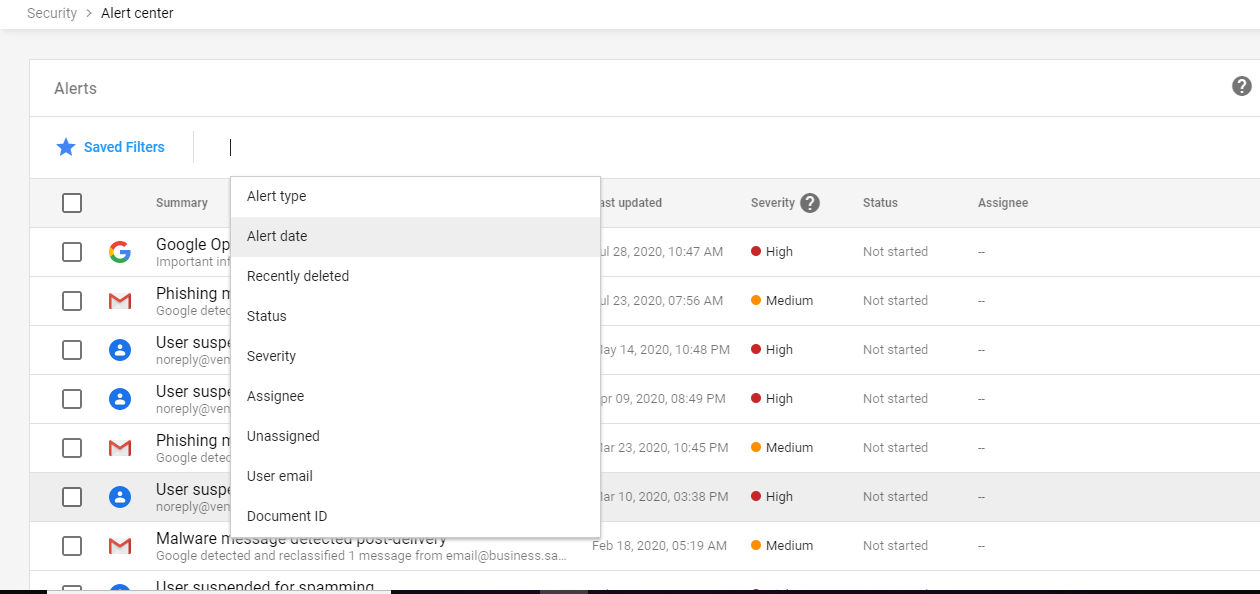
Alert Center – View important and actionable notifications about potential security issues within your domain. On expanding Alert Center you can view a list of alerts generated with severity levels High, Medium and Low. You can also filter those alerts using the available parameters shown below. On clicking each alert, a detailed description of the alert should be displayed in a new tab, and you remediate the action for the alert. From there you can assign a user for that alert to look upon further. You can also delete the alert if it is not necessary or remediate action already taken.
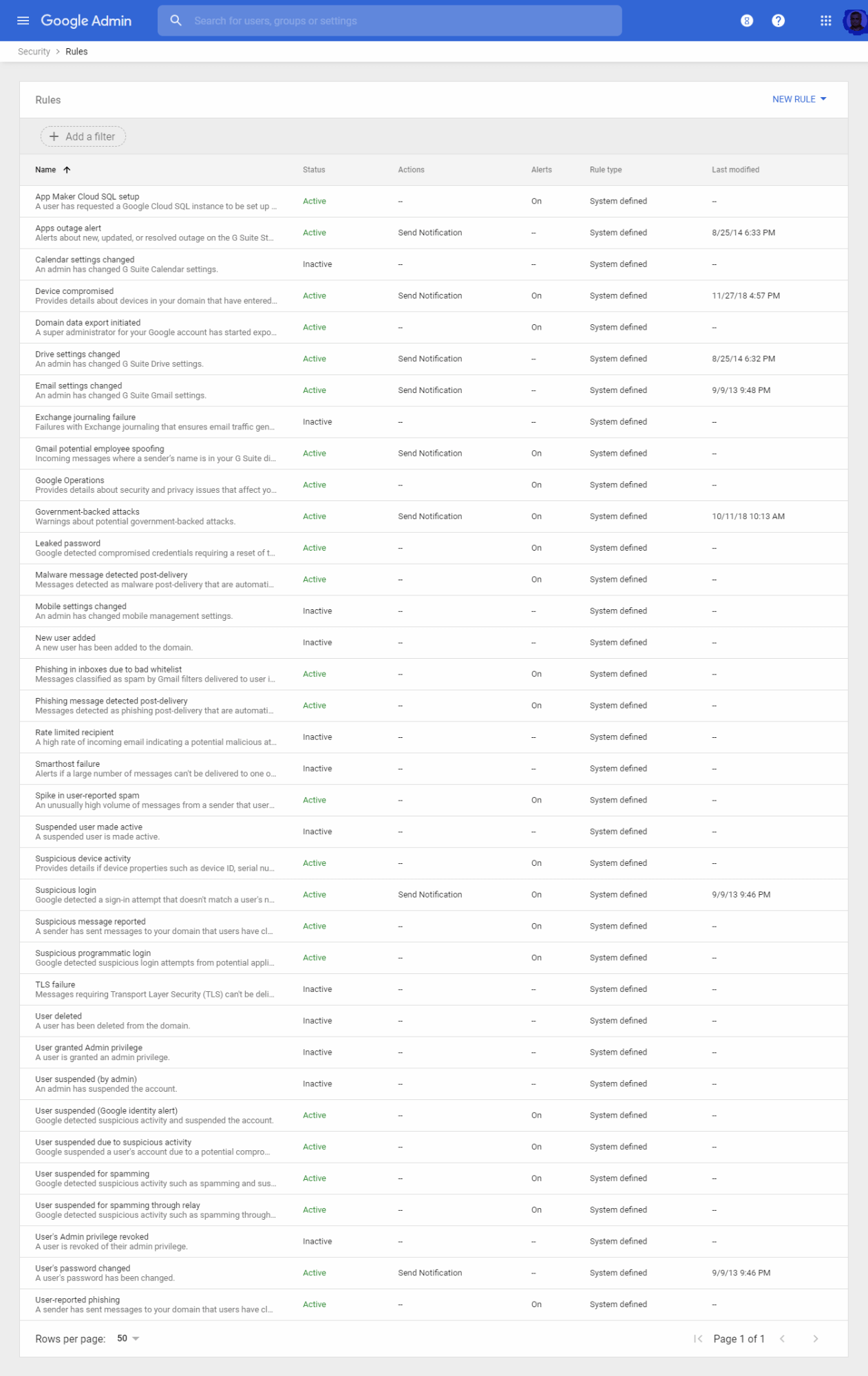
Security rules – Using this you can manage system defined and custom-created rules including notification settings. You can see a collection of predefined rules with status ( Active / Inactive ) mode and Actions to be carried out. Anytime you can edit the rule, change the status and can set send notifications to all Super administrators or to any user. While editing you will be provided with information about rule details and scope, Conditions, Actions, and Review. You can also add a new rule based on the Audit log generated.
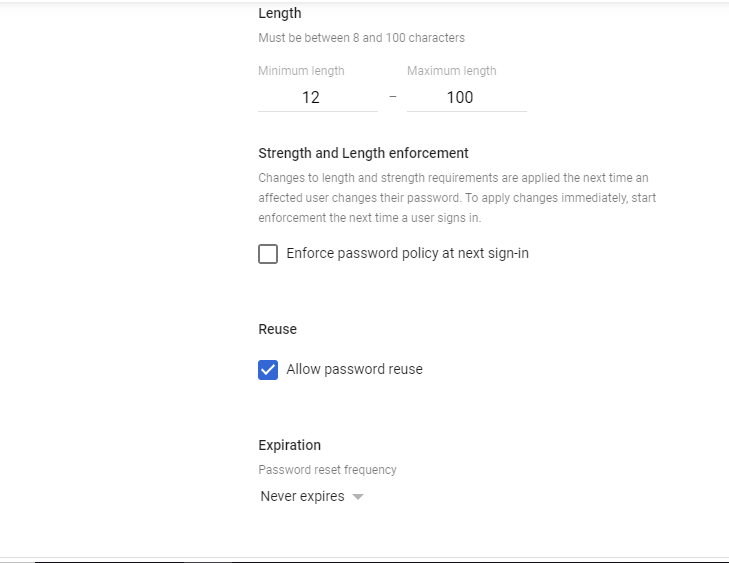
Password Management – Configure password policies for your organization. Here you can set the settings for Strength, Length, and Expiration of all user’s passwords. You can enforce to use a Strong password by enabling the “Enforce strong password” setting. You can set the length of the password to use, so the minimum character required to set a password for all users. By default, it is between 8 characters to 100 characters. You can edit this setting to change to 12 or 16 characters to enforce a strong password for your users on their next sign-in.
You can also enable or disable to reuse the password for your users. Also, you can set a period of time to reset the user’s password on day intervals of 30days, 60days, 90days, 180days, and 365days.
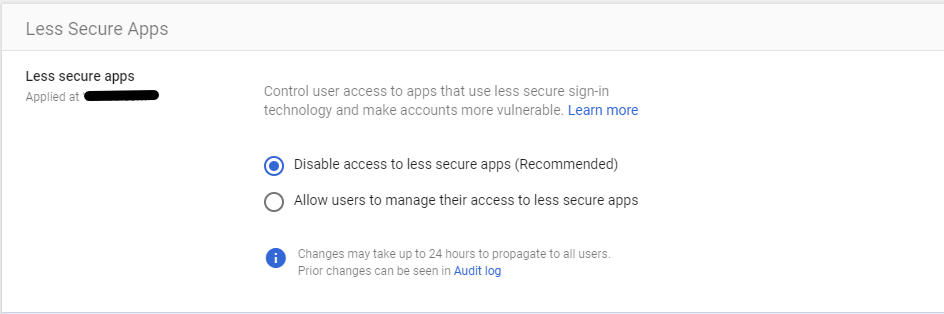
Less secure apps – Configure policies to manage access to less-secure applications. These settings control user access to applications that use less secure sign-in technology and make accounts more vulnerable. By default, the recommended setting is Disable access to less secure applications. You can disable these settings at the domain level or OU level. Even you can go to the individual user’s security tab and set these settings to override the domain level change.
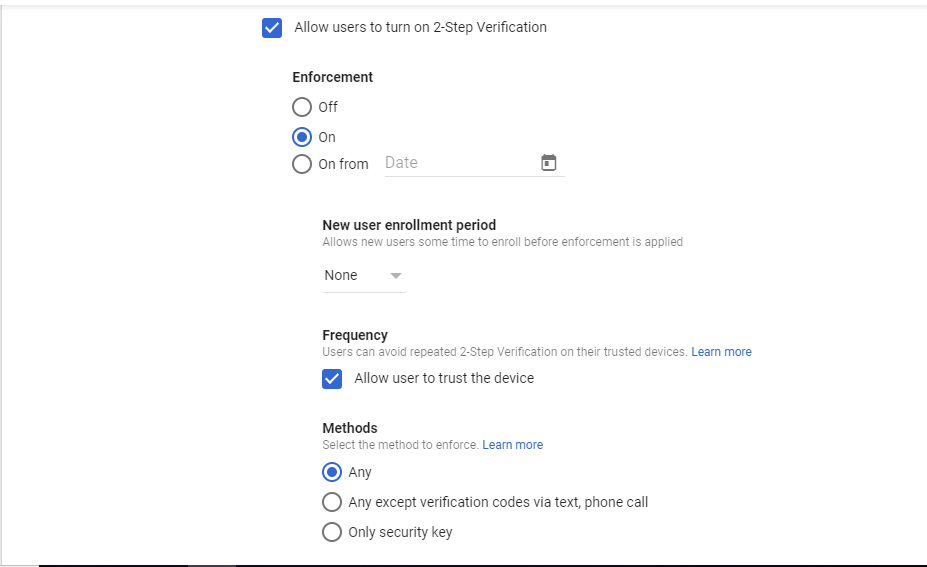
2 Steps verification – Configure 2-Step Verification policies for all users when they log in using their username and password. This will add an extra layer of security to user accounts by asking users to verify their identity when they enter a username and password.
You can enforce 2 step verification settings ON forever or from a particular date. You can allow the user to trust a device that will not be asked for 2 step verification repeated by during sign in.
Also, you can choose the method to use for 2 step verification. Either can be used to send verification code to mobile devices via text or a call. Or you can set a verification key ( security key ) for individual users. Security codes are single-use codes that can be used where security keys are not supported. You can allow users to generate their keys or you can set it for them.
Account Recovery – In this settings, you can configure account-recovery policies. In this Account Recovery settings, you can set account recovery for the Super Admin account and User account.
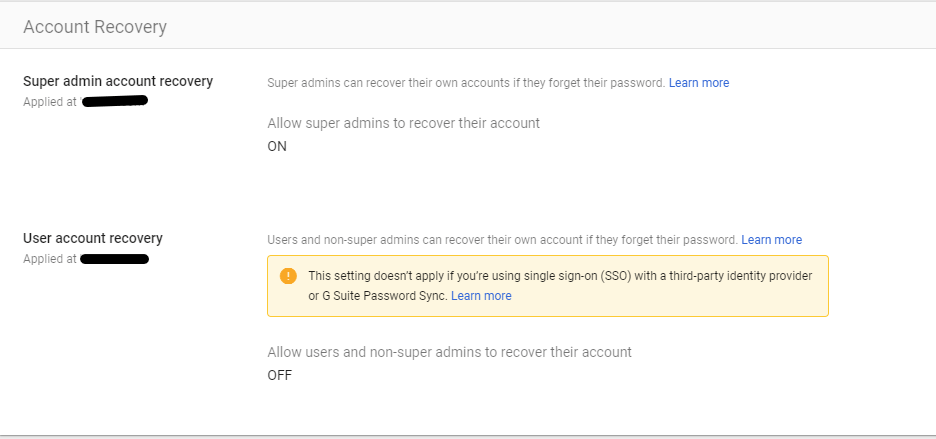
Note: If you are using SSO with a third-party identity provider or using GSuite Password Sync, you cannot set User account recovery. Admin accounts can set or reset the password for individual users.
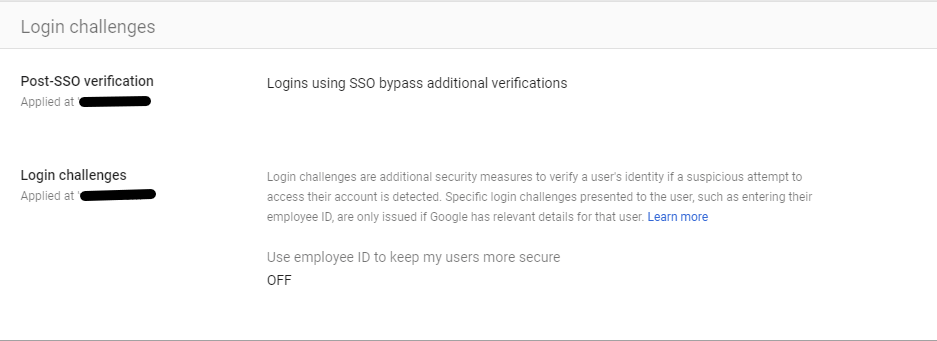
Login challenges – Manage the information used during login to protect users. Post SSO verifications and Login challenges settings are managed here. If you’ve configured Single Sign-On, Google may still want to present users with Login challenges after they return from your Identity Provider when there’s something suspicious about the login.
Login challenges are additional security measures to verify a user’s identity if a suspicious attempt to access their account is detected. Specific login challenges presented to the user, such as entering their employee ID, are only issued if Google has relevant details for that user. You can enable the setting “ Use employee ID to keep my users more secure” in this Login challenge settings.
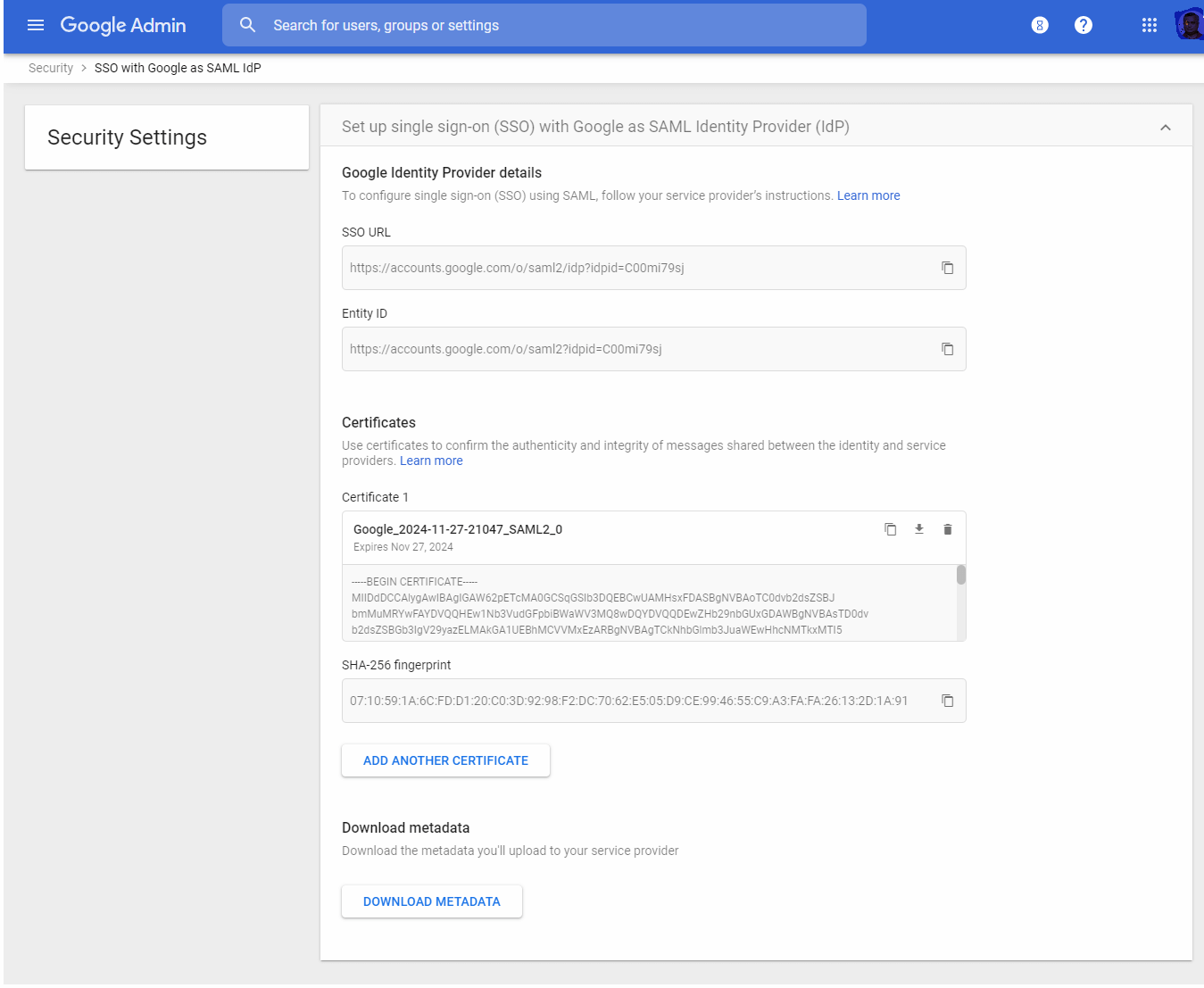
Setup SSO for SAML applications – Set up single sign-on for third-party applications with Google as the identity provider. Here you will have the details of Google SSO URL and Entity ID to setup SSO with Google as SAML Identity Provider.
Here you can upload additional certificates to confirm the authenticity and integrity of messages shared between the identity and service providers.
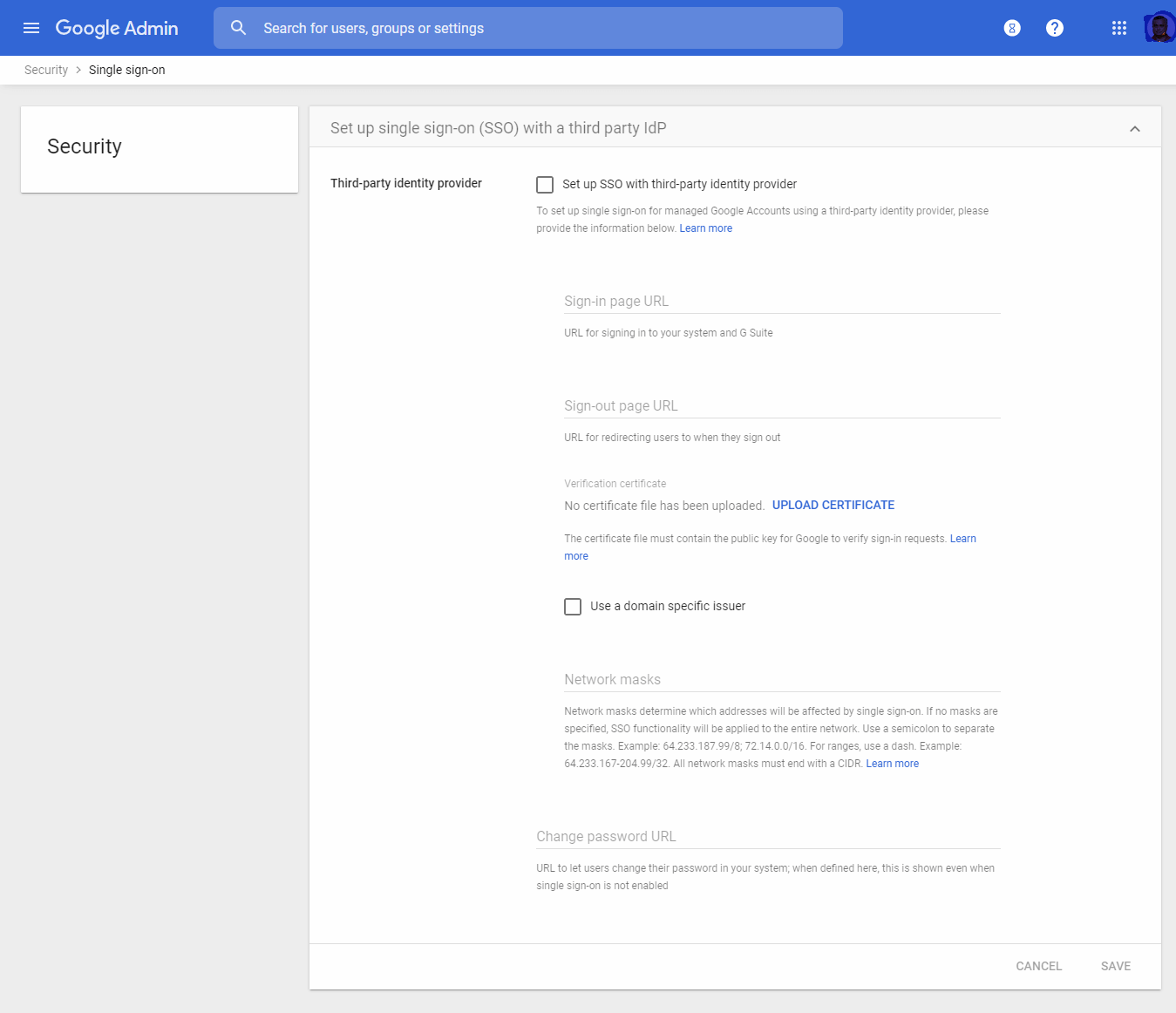
Setup SSO with a third-party Identity Provider IdP – In this control page you can set up single sign-on for managed Google Accounts using a third-party identity provider.
To set up a single sign-on for managed Google Accounts using a third-party identity provider, the administrator should provide a sign-in page URL, sign out page URL, and change password URL here. You need to upload a verification certificate here. This certificate file must contain the public key for Google to verify sign-in requests
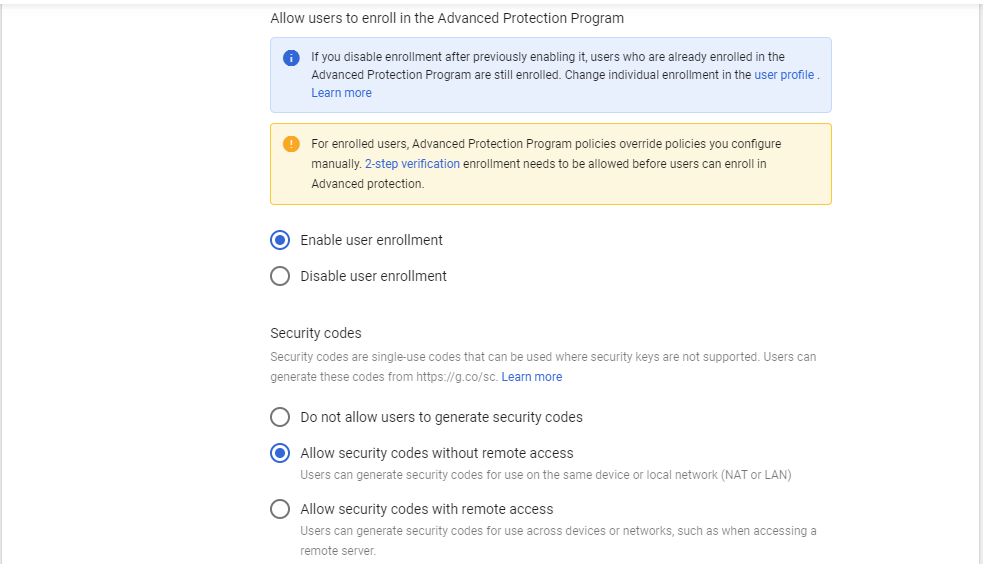
Advanced Protection Program – This security setting enables an advanced protection program to safeguard the Google accounts of users who are at the risk of targeted attacks from the outside world. Administrators can enable or disable the Advanced Protection Program domain-wide.
Security codes are single-use codes that can be used where security keys are not supported. Users can generate these codes from Google Advanced Protection Program control panel.
Context-aware access – Use device and user identification to manage access levels and enforce access policies for G Suite applications. Context-Aware Access is only available with G Suite Enterprise, Cloud Identity Premium, and G Suite Enterprise for Education.
Only super admins and delegated admins with appropriate privileges can manage Context-Aware Access. Resellers can’t manage Context-Aware Access for their customers
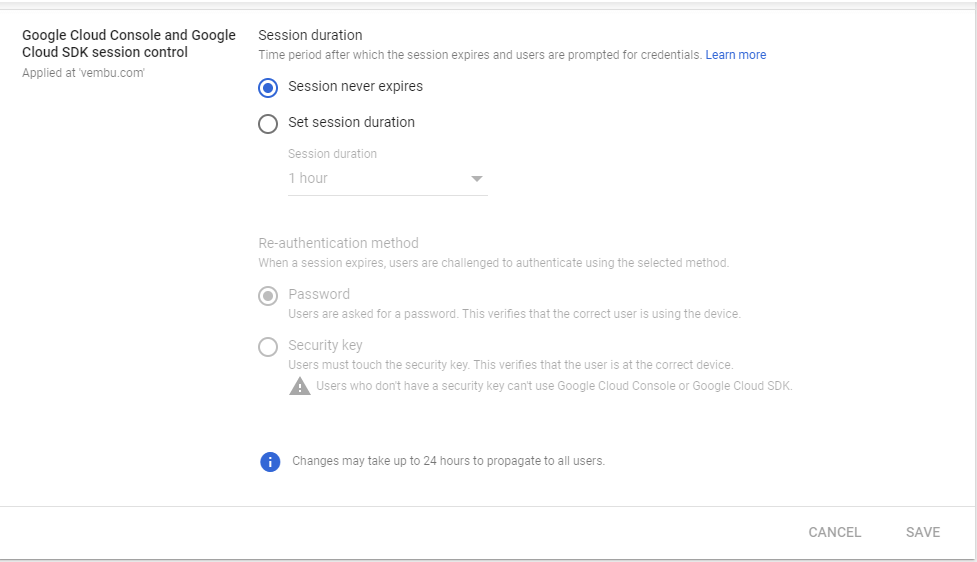
Google Cloud session control (Beta) – Set session duration for Google Cloud Platform Console and Google Cloud SDK. You can set the time period after which the session expires and users are prompted for credentials. Session duration can be from 1 hour to 24 hours per day, or even you can make it never expire.
Advanced Settings API Permission – Manage advanced security features, such as authentication and integrating G Suite with internal services. These advanced features include App access control through API and Domain-wide delegation settings. Using this App access control, administrators can enable or restrict access to G Suite APIs for customer-owned and third-party applications and service accounts. Reduce the risk associated with third-party access to G Suite APIs by limiting access to only trusted apps.
Domain-wide delegation – Developers can register their web applications and other API clients with Google to enable access to data in Google services like Gmail. You can authorize these registered clients to access your user data without your users having to individually give consent or their passwords.
Conclusion:
GSuite provides this kind of readily available security checklist for medium and large enterprises having more than 100+ users. IT administrators for medium and large businesses should follow these security best practices to help strengthen the security and privacy of company data. You’ll use one or more settings in the Google Admin console to implement each best practice available in this checklist. Also note that to help protect your business, Google turns on many of the settings recommended in this checklist as security best practices by default.
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.



Leave A Comment