What is AWS Certificate Manager ( ACM )?
AWS Certificate Manager is a service that lets you easily provision, manage, and deploy public and private Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates for use with AWS services and your internal connected resources. SSL/TLS certificates are used to secure network communications and establish the identity of websites over the Internet as well as resources on private networks. AWS Certificate Manager removes the time-consuming manual process of purchasing, uploading, and renewing SSL/TLS certificates.
Table of Contents
- What is AWS Certificate Manager ( ACM )?
- How does ACM work?
- Accessing AWS Certificate Manager in AWS console
- Requesting an SSL/TLS certificate
- Deleting a Certificate
- Importing a Certificate
- Conclusion
As far as SSL/TLS certificates deployment is concerned, AWS offers two options to the customers, they can choose either of these to best suit their needs.
AWS Certificate Manager (ACM) — This service is for enterprise customers who need a secure web presence using TLS. ACM certificates are deployed through Elastic Load Balancing, Amazon CloudFront, Amazon API Gateway, and other integrated AWS services. The most common application of this kind is a secure public website with significant traffic requirements. ACM also simplifies security management by automating the renewal of expiring certificates.
ACM Private CA — This service is for enterprise customers building a public key infrastructure (PKI) inside the AWS cloud and intended for private use within an organization. With ACM Private CA, you can create your certificate authority (CA) hierarchy and issue certificates with it for authenticating users, computers, applications, services, servers, and other devices. Certificates issued by a private CA cannot be used on the internet. For more information, see the ACM Private CA User Guide.
How does ACM work?
According to the AWS documentation, ACM can works to
- Request or import a TLS/SSL certificate you would like to use into your AWS account
- Validate domain ownership for your requested certificate using Domain Name System (DNS) or email validation to complete certificate issuance
- Use your newly issued or imported certificates in various AWS services like Elastic Load Balancing (ELB), Amazon CloudFront etc
In this blog, we are providing an overview of steps involved in requesting a public certificate from Amazon or a private certificate from the organization’s certificate authority (CA).
Accessing AWS Certificate Manager in AWS console
Login to AWS console using root user credentials or an IAM user credential with administrative privileges.
Choose under Services → Security, Identity & Compliance → AWS Certificate Manager.
This will list all the certificates if you already created under a particular region or will show a similar screenshot that will allow you to request a new certificate or import a certificate or create a private CA.
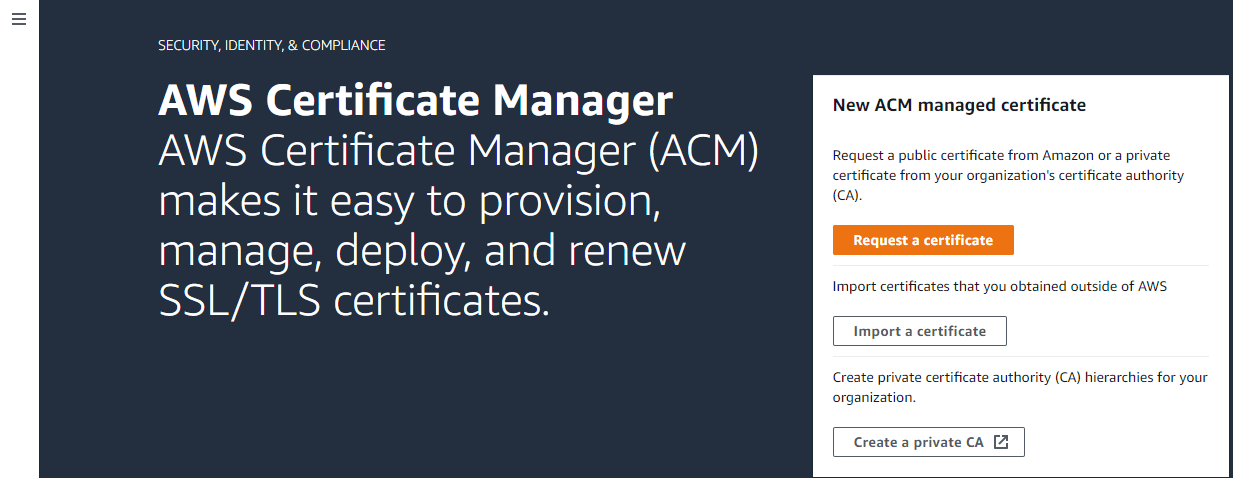
Requesting an SSL/TLS certificate
In the first step, we are going to request a public SSL/TLS certificate for a domain to establish secure communication access across the internet. Click Request a certificate button to proceed,
On the next screen, choose “Request a public certificate” as shown below. Here note that requesting a private certificate is grayed out because requesting a private certificate requires the creation of a private certificate authority (CA). To create a private CA, one must visit the ACM Private Certificate Authority link page shown.
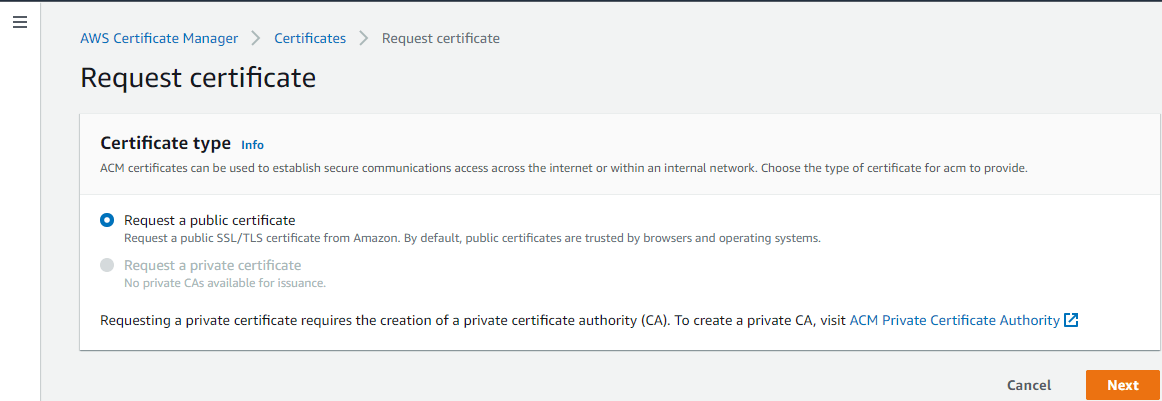
Click Next to proceed
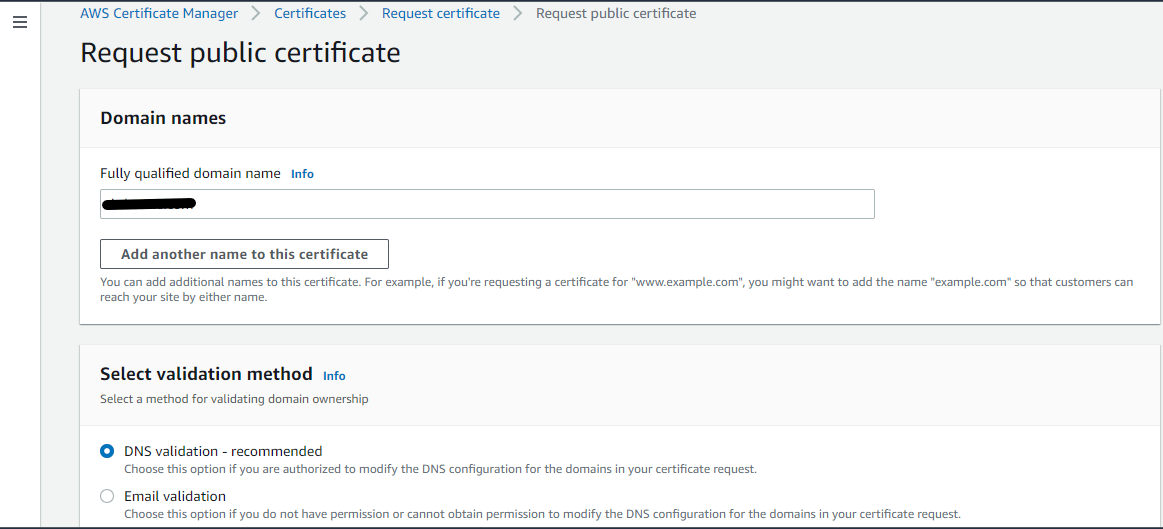
In the next step, users need to provide the fully qualified domain name (FQDN) in the box. You may also add the name to the party certificate. For example, if you’re requesting a certificate for “www.example.com”, you might want to add the name “example.com” so that customers can reach your site by either name.
In the domain validation section, choose “DNS validation” as shown in the below screenshot. Choose this option if you are authorized to modify the DNS configuration for the domains in your certificate request. Another option is “Email validation” if you do not have permission or cannot obtain permission to modify the DNS configuration for the domains in your certificate request. Here we have the permission to modify the DNS configuration of the domain in the domain registrar control panel.
In the tag section, you may provide the tag key and tag value which is an optional step. Click the “Request” button to proceed to the next step
Now you can see a successful request message as shown below, and you have the option to view the certificate.
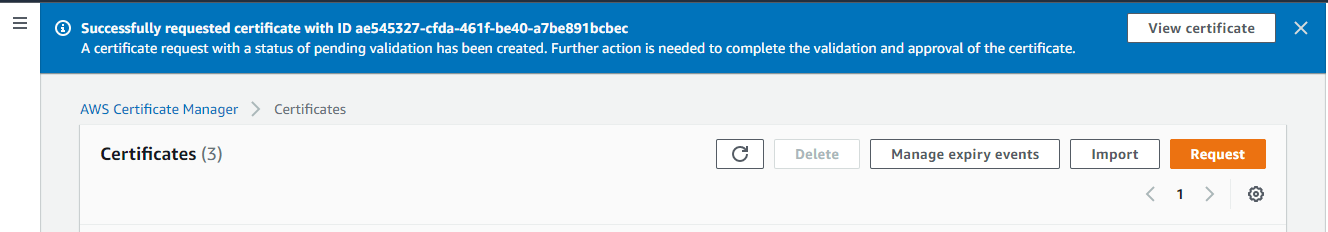
In this Certificates section, you can view the newly added domain with the status “Pending validation as shown in the below screenshot. Before the Amazon certificate authority (CA) can issue a certificate for the domain we have mentioned in the previous step, AWS Certificate Manager (ACM) must prove that you own or control all of the domain names that you specify in your request.
On clicking the particular certificate, one can view the CNAME name and CNAME value for the domain to validate. Users can enter the CNAME name and CNAME value in the respective domain DNS section in their registrar DNS control panel, user can validate the domain manually.
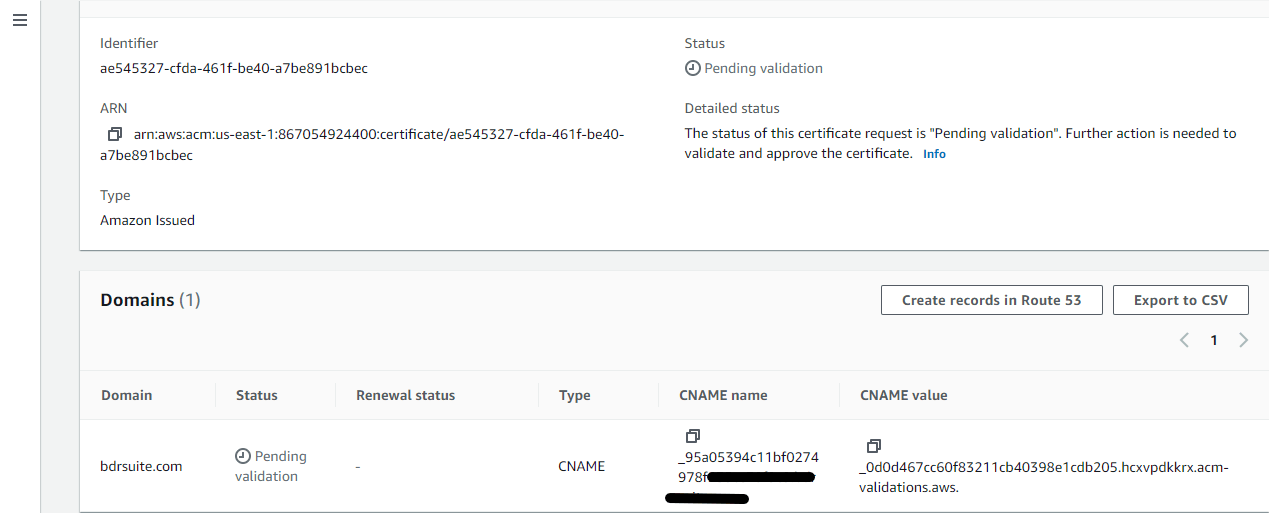
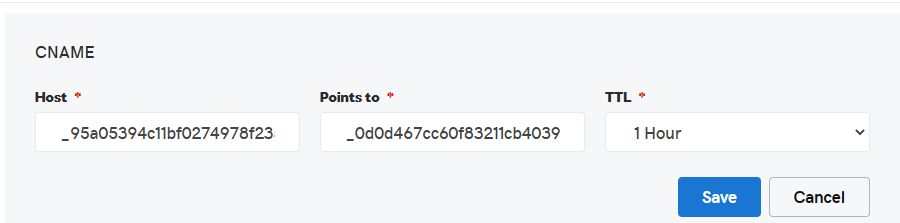
Create a CNAME record with the value of CNAME name ( Copy the content without the trailing domain name and paste in “Host” column in the DNS control panel ) & Copy the CNAME value and paste in the “Points to” column as shown in the below screenshot. Click Save and add this CNAME record.
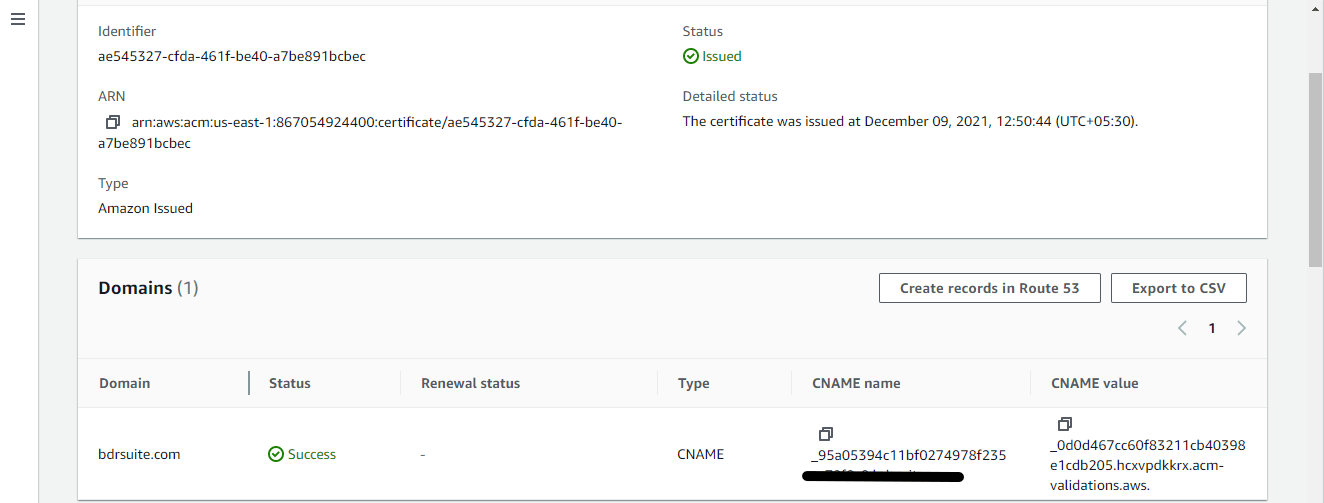
After adding the CNAME record, domain validation happens automatically after a few minutes, and you can verify this validation by the status changed from “Pending validation” to “Success” as shown in the screenshot below. Also, you can see the certificate status changed from “Pending validation” to “Issued” ( Shown in Redbox in the screenshot below )
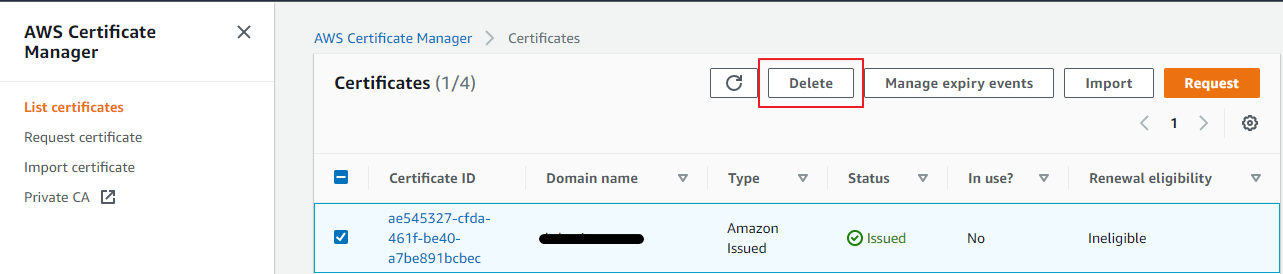
You can also delete the certificate, in case of an expired certificate period or would like to discard the domain. In such a case, you can delete the certificate from the “List Certificate” page by selecting the certificate name and by clicking the Delete button. The below screenshot shows in detail.
A confirm dialog asks you to enter the text “delete” to confirm the delete process.
Using this option, you can import certificates that you obtained outside of AWS. To import a self–signed SSL/TLS certificate into ACM, you must provide both the certificate and its private key. To import a certificate signed by a non-AWScertificate authority (CA), you must also include the certificate chain, but not a private key. Your certificate must satisfy the following criteria listed below.
For all imported certificates, you must specify a cryptographic algorithm and a key size. ACM supports the following algorithms (API name in parentheses):
- 1024-bit RSA (RSA_1024)
- 2048-bit RSA (RSA_2048)
- 3072-bit RSA (RSA_3072)
- 4096-bit RSA (RSA_4096)
- Elliptic Prime Curve 256 bit (EC_prime256v1)
- Elliptic Prime Curve 384 bit (EC_secp384r1)
- Elliptic Prime Curve 521 bit (EC_secp521r1)
When importing a certificate, the user must need a Certificate body & Certificate Private key and optionally need a Certificate chain. The certificate, private key, and certificate chain must be PEM–encoded. The below screenshot shows these details. Here we are not importing any third-party certificates, and provide an overview of the steps involved in it.
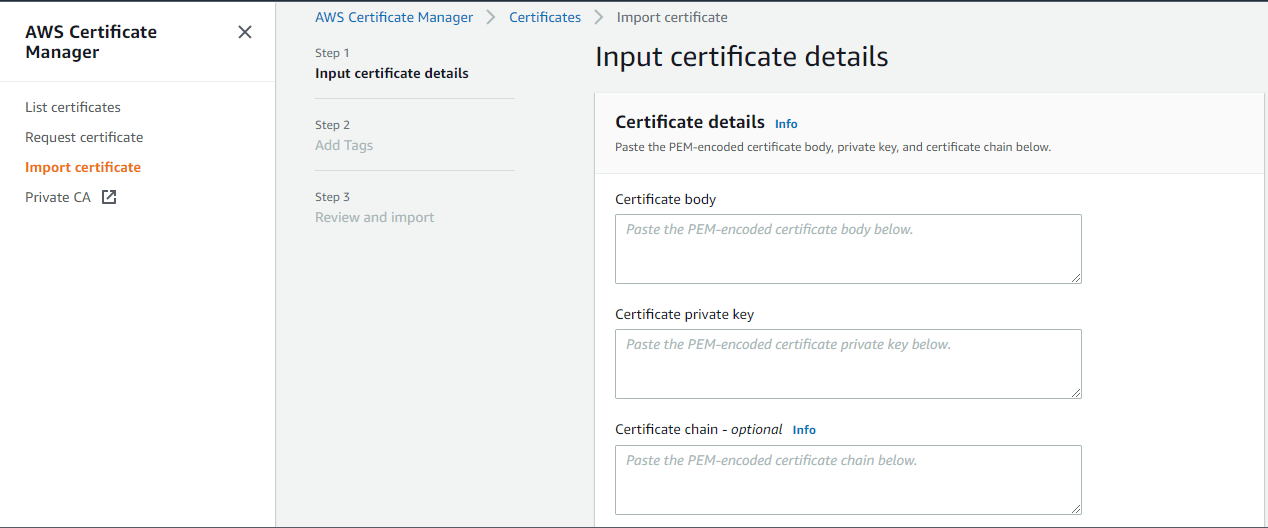
Click Next to add tags, and on the third step review the content you added and import the key to AWS Certificate Manager. Below considerations are required when you import a third-party certificate.
- The certificate must specify a cryptographic algorithm and a key size
- The certificate must be an SSL/TLS X.509 version 3 certificate
- The private key of an imported certificate must be no larger than 5 KB (5,120 bytes)
- The cryptographic algorithm of an imported certificate must match the algorithm of the signing CA
Conclusion:
The main benefits of using AWS Certificate Manager are “Free public certificates for ACM-integrated services” and “Get Certificate easily”. With AWS Certificate Manager, there is no additional charge for provisioning public or private SSL/TLS certificates you use with ACM-integrated services, such as Elastic Load Balancing and API Gateway. You pay for the AWS resources you create to run your application. AWS Certificate Manager removes many of the time-consuming and error-prone steps to acquire an SSL/TLS certificate for your website or application. There is no need to generate a key pair or certificate signing request (CSR), submit a CSR to a Certificate Authority, or upload and install the certificate once received. With a few clicks in the AWS Management Console, you can request a trusted SSL/TLS certificate from AWS. Once the certificate is created, AWS Certificate Manager takes care of deploying certificates to help you enable SSL/TLS for your website or application.
Related Posts:
vCenter certificate replacement and Lookup service
How to Install Active Directory Certificate Services (AD CS) in Windows Server 2016
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.



Leave A Comment