Introduction
What is MFA?
MFA is an electronic authentication method in which a device user is granted access to a website or application only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism. MFA protects the user from an unknown person trying to access their data such as personal ID details and all his data. Passwords can be implemented through token sharing methods such as mobile phone-based authentication. Some methods include push-based authentication, QR code-based authentication, one-time password authentication (event-based and time-based), and SMS-based verification method.
MFA in Microsoft Office 365
Multifactor authentication (MFA) in Microsoft Office 365 adds a layer of protection to the sign-in process of Office 365 users. Users provide additional identity verification when accessing accounts or apps, users provide additional identity verifications. In this blog, we are detailing the steps to enable MFA authentication for Office 365 users in Microsoft 365 Admin control panel.
Enabling MFA for Office 365 users in Microsoft 365 Admin center
Login to Microsoft 365 admin Center using a Global administrator account or a privileged administrator account using its credentials. On the left side expand the Users list, and choose Active users. On the right side choose Multi-factor Authentication from the list shown in the below screenshot.
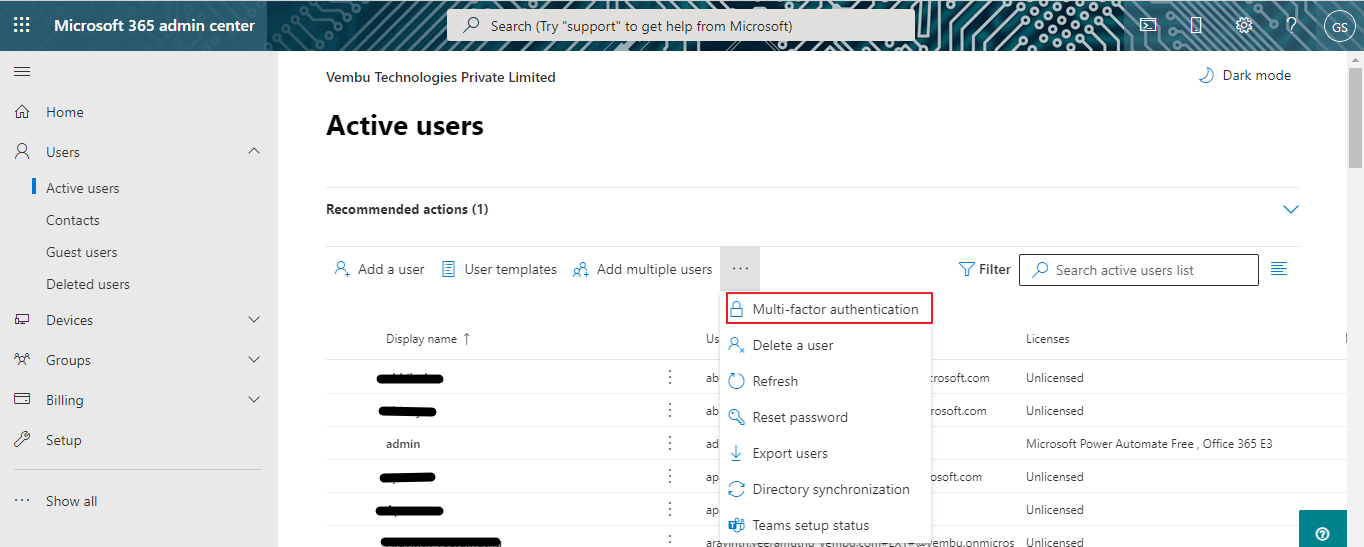
On clicking the Multi-factor authentication button, a new screen will appear, showing the lists of users and multi-factor authentication status. Usually, the authentication status will be shown as disabled, as all the listed users are not multifactor enabled users. Select all the users and click Manage user settings on the right side, as shown in the red box in the below image.
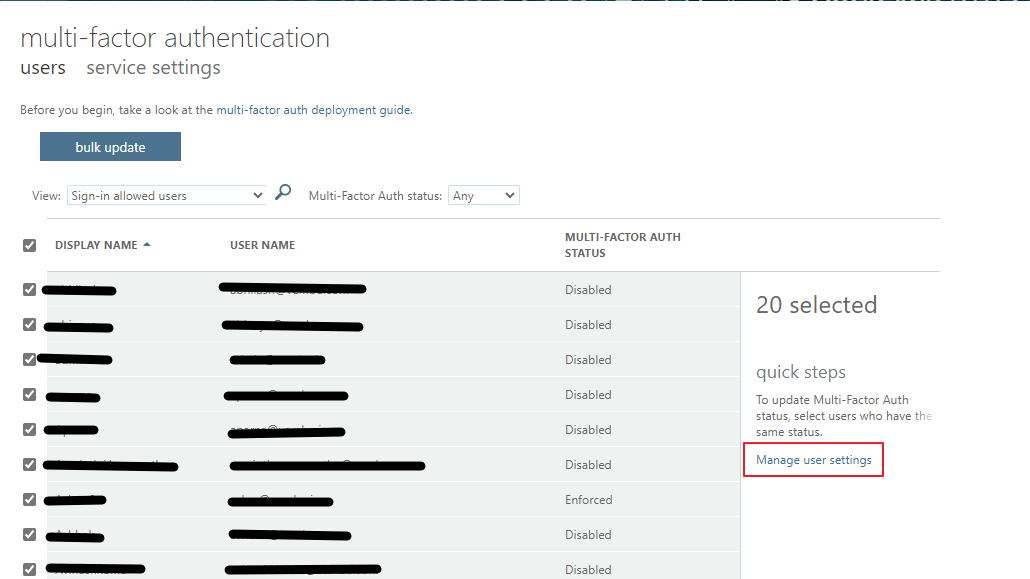
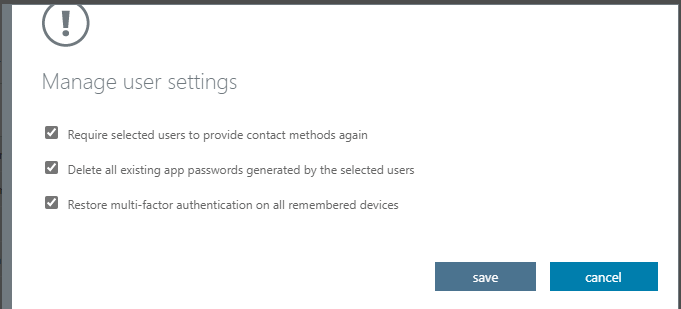
Clicking “Manage User settings”, will open a new pop-up, the end-users to enable the options listed there. The available options are :
- Require selected users to provide contact methods again
- Delete all existing app passwords generated by the selected users
- Restore multi-factor authentication on all remembered devices
Administrators can enable all the above settings or choose any of these settings depending on their requirements. For the first-time enablement, you can enable all the above options as shown in the below screenshot, and choose to save.
This will update all the selected user’s MFA settings into enable state. And on the next login, each user can be authenticated through the MFA method.
Multifactor Authentication Service settings
On this page, the Administrator can customize the MFA settings for the end-user experience. Available service settings are,
App password settings – These settings allow/prevent the user to create app passwords to sign in to non-browser apps. You can allow or prevent the settings by choosing the button.
Trusted IPs – The Trusted IPs feature of Microsoft Office 365 Multi-Factor Authentication bypasses multi-factor authentication prompts for users who sign in from a defined IP address range. You can set trusted IP ranges for your on-premises environments so when users are in one of those locations, there’s no MFA prompt. Administrators can assign their trusted IPs in the available box. Usually, a the devicesTheseClickinguser-user, administrators can put the firewall IPs on the trusted box so that users will not get an MFA prompt when they are connected to the Office network.
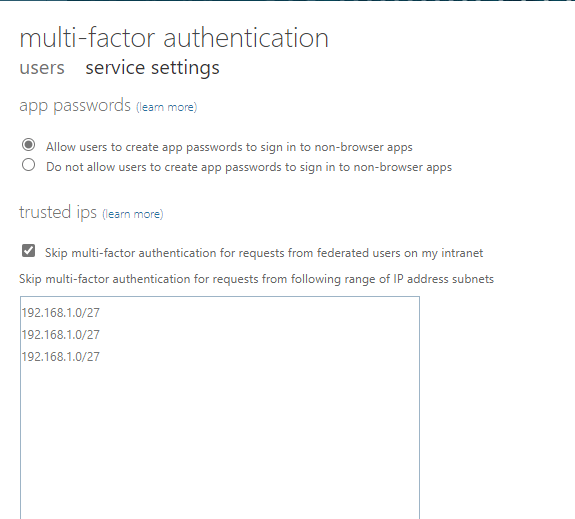
Verification options – Here you can enable the verification methods to implement MFA for the Microsoft Office 365 users.
Methods available to users:
- Call to phone
- Text message to the phone
- Notification through a mobile app
- Verification code from mobile app or hardware token ( can be a USB security hardware key attached to the computer device )
Administrators can enable all the above settings
Remember multi-factor authentication on trusted device send-user settings allow users to remember multi-factor authentication on devices they trust (between one to 365 days). Administrators can put any days in the mentioned box. By default 90 days.
The below screenshot shows these two settings.
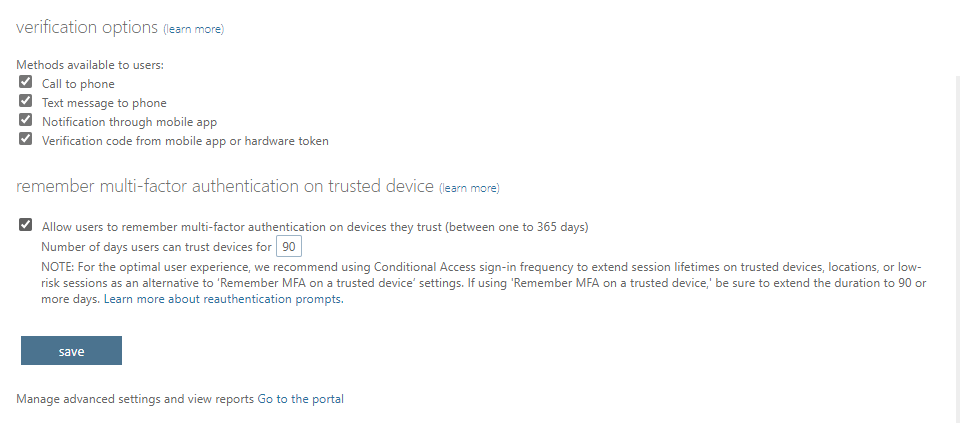
Click save to enable the settings we configured.
Note: The above-covered steps to Enable MFA for Microsoft Office 365 users only, not for Azure AD users. There will be separate steps for enabling MFA for Azure AD users through the Azure AD portal, and this is not covered in this blog.
Conclusion :
In a nutshell, MFA reduces the risk of a security breach drastically, and sensitive data stays protected. The primary benefit of multi-factor authentication is that it provides additional security layers and decreases the chance of consumer identities becoming compromised. Since MFA integrates with Microsoft Office 365 SSO engine, You no longer have to create multiple complex passwords for different applications. Using a secondary authentication with SSO confirms the consumer identity and removes the multiple entries of passwords for different applications. In simple steps, an Administrator can enable or invoke the MFA settings for a particular user in a few minutes in the Microsoft 365 Admin control panel.
Download to try our 30-day free trial!
Protect your Microsoft 365 data with Vembu Backup for Microsoft 365 now!
Download the full-featured 30-day free trial of our latest version Vembu BDR Suite v4.2.0 and experience modern data protection for your Office 365 environment.
Learn about Vembu Backup for Microsoft 365 here.
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.



Leave A Comment