Table of Contents
- Default Windows Firewall Allowances and Behavior
- Additional Remote Management Firewall Access Configuration
- Enable Remote Desktop in Hyper-V
- Enabling PowerShell Remoting in Hyper-V
- Enabling other Hyper-V Remote Services for Management
- Configure Hyper-V Windows Server Firewall and Remote Management with Group Policy
- Concluding Thoughts
One of the first things that Hyper-V administrators will want to do after standing up Hyper-V hosts joined to a Windows Server Failover Cluster is to enable basic remote utilities for managing Hyper-V hosts. Windows Server contains the Windows Firewall which provides a great way to further secure network connectivity to Hyper-V hosts. Firewall configuration must be taken into consideration with remote administration. The Windows Server Firewall by default will allow all Hyper-V cluster specific traffic to be communicated. This means the administrator does not have to make any allowances for the cluster roles to be able to communicate with each other. Additionally, Hyper-V administrators will be able to make connections using some of the expected management utilities.
- Which management applications are allowed to communicate by default?
- What Windows Firewall remote management specific configuration needs to be enabled to allow further remote administration?
- What other tools may Hyper-V administrators want to be able to use to remotely administer Hyper-V hosts in a Windows Server Failover Cluster?
Let’s take a look at the Hyper-V Basic Remote Management Firewall Configuration.
Default Windows Firewall Allowances and Behavior
By default, there are allowances to use some of the basic Hyper-V management utilities to manage and configure Hyper-V hosts. These allowances include the ability to use Server Manager, Hyper-V Manager, and Failover Cluster Manager. The default Hyper-V virtual switch is a uniquely configured piece of virtual infrastructure as relates to the Windows operating system and the Firewall specifically. With the Hyper-V switch, nothing else is bound to the virtual switch including network protocols. This is why the management operating system has no visibility into the Hyper-V virtual switch. Also, it accounts for the fact that Firewall configuration on the operating system has no effect on the Hyper-V traffic flowing across including virtual machine traffic passing in and out.
Additional Remote Management Firewall Access Configuration
Aside from the default management utilities such as Server Manager, Hyper-V Manager, and Failover Cluster Manager, there will most likely be other remote management utilities you will want to allow to access the Hyper-V host. These include enabling the following remote administration services as well as perhaps disabling the Windows Firewall altogether.
- Remote Desktop
- PowerShell
- Various Services
- File and Print Sharing
- Ping
- Remote Disk Management
- Disabling the Firewall
Let’s take a quick look at enabling the above-mentioned remote administration capabilities and how this is accomplished with the Windows Firewall.
Enable Remote Desktop in Hyper-V
Remotely administering Windows Server Hyper-V either in the Desktop GUI version or in the Server Core variant can easily be done with a Remote Desktop connection. Windows Server administrators have long used Remote Desktop as a means to remotely manage and configure Windows Servers. RDP allows administrators to have basically the same experience they would have if they were sitting at the console of a server, performing administration tasks.
What about the Windows Server Core? Can you use Remote Desktop to administer a Core installation?
Yes.
Remote Desktop connections to Windows Server Core present the Windows Server Core desktop in the same fashion as sitting at the console. Administrators can interact with sconfig.cmd, the command line driven configuration utility, the same way in the RDP session.
Using the sconfig.cmd utility, you can easily enable the Remote Desktop connection to your Windows Server Core Hyper-V host.
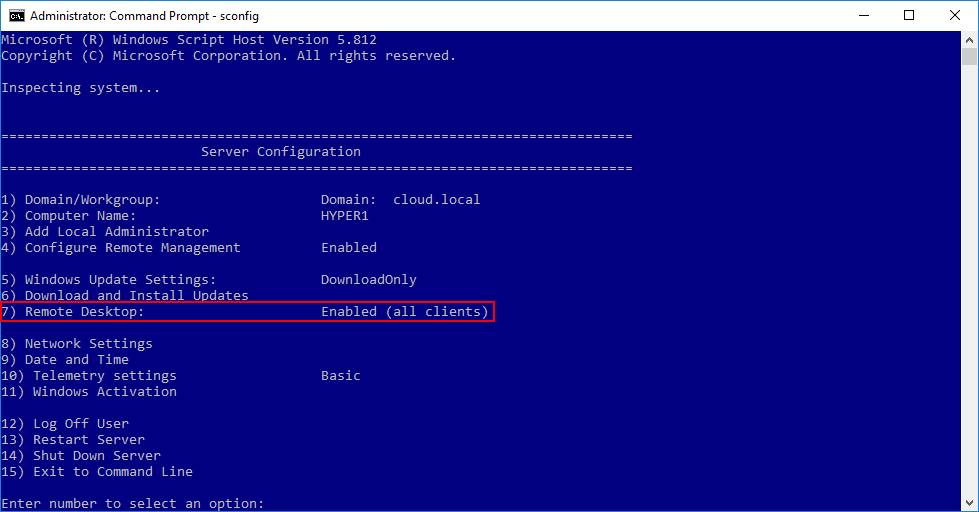
Selecting to Enable the Remote Desktop services on a Windows Server Core Hyper-V host. By enabling Remote Desktop, Windows Server Firewall rules for RDP are automatically enabled.
Once Remote Desktop is enabled on the Windows Server Core installation, you can RDP into the Server Core installation and see the sconfig utility and interact with it as needed.
Enabling PowerShell Remoting in Hyper-V
PowerShell Remoting is a powerful way to interact with today’s Windows Server installations, including Hyper-V hosts. PowerShell Remoting allows remotely running PowerShell commands against a Windows Server host as if you are on the Hyper-V host itself.
This can be enabled via the sconfig interface via option number (4).
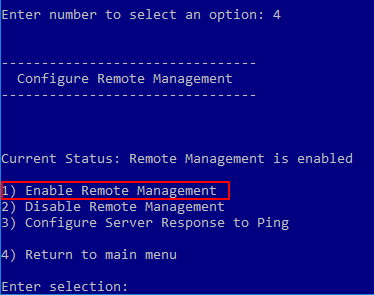
You can also enable PowerShell remoting via the PowerShell command line.
- Enable-PSRemoting -Force
Enabling other Hyper-V Remote Services for Management
There are a few other services that you may want to enable for remote management of a Hyper-V host running Windows Server firewall. These include:
- Ping
- File and Print Services
- Remote Disk Management
- Disabling the Firewall altogether
Hyper-V Ping Enable
You can enable ping on a Hyper-V host via the netsh command line utility.
- netsh firewall set icmpsetting 8
- netsh firewall set icmpsetting 8 disable
- netsh advfirewall firewall add rule name=”ICMP Allow incoming V4 echo request” protocol=icmpv4:8,any dir=in action=allow
File and Print Sharing
File and Print Sharing services are extremely handy if you are wanting to copy files over to the Hyper-V host. You can also use netsh to enable this connectivity by using the following:
- netsh advfirewall firewall set rule group=”File and Printer Sharing” new enable=Yes
Enabling Remote Disk Management
There can be times when remote disk management can be helpful for certain configuration especially in the initial setup phase for a Hyper-V host. You can enable this via the following:
- netsh advfirewall firewall set rule group=”Remote Volume Management” new enable=yes
Disabling the Windows Firewall
There may be a use case for you to disable the Windows Firewall altogether. Some organizations disable local firewalls, and some choose to utilize these as part of their overall security stance. Even if the Windows Firewall is something you want to use on the Hyper-V host, it may be that again during the initial setup or configuration phase, you just want to disable it. This can prevent the local Windows Firewall from impeding progress in configuring or remote administration during the initial setup.
To disable the Windows Firewall using the command line, use the following command:
- netsh advfirewall set allprofiles state off
Configure Hyper-V Windows Server Firewall and Remote Management with Group Policy
Group Policy provides a great way to automatically configure customized Windows Firewall settings for all Hyper-V hosts. You can create a policy applied to Hyper-V hosts that disable the Firewall or adds custom exceptions.
Disable
Navigate to Computer Configuration >> Policies >> Network >> Network Connections >> Windows Firewall >> Domain Profile >> Windows Firewall: Protect all network connections > Disabled.
Granular Exceptions
Navigate to Computer Configuration >> Policies >> Windows Settings >> Security Settings >> Windows Firewall with Advanced Security >> Windows Firewall with Advanced Security. Right-click the Inbound Rules and add the New Rule to create rules.
- Remote Desktop – use the Predefined dot and Remote Desktop from the drop-down box
- PowerShell – Same as RDP but select Windows Remote Management
- Remote Service Management – Can be selected in the Predefined drop-down
Concluding Thoughts
Windows Server Firewall is a powerful built-in mechanism for securing Windows Server environments. This includes Hyper-V hosts. The Firewall is a free offering that comes with Windows. When configuring Hyper-V, administrators must take the Windows Firewall into account for remote configuration and management purposes. By default, the core Windows Server Failover Cluster services can communicate as well as the standard Hyper-V tools. These include Hyper-V Manager, Failover Cluster Manager, and Server Manager. Other remote configuration and management utilities will have to be allowed through the Windows Firewall. Using the sconfig utility with Windows Server Core, many of these are easily configured such as RDP and remote management using PowerShell. Additional connectivity such as disk management, ping, file and printer sharing, and others can be easily configured with the command line with netsh.
Related Posts
Configuring RADIUS Authentication in Windows Server 2016 AD – Sonicwall
How to Secure your Data Backups – A Comprehensive guide
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.



Leave A Comment