Formerly known as the Hardening Guide, the Security Configuration Guide (SGC) provides a set of guidelines aimed at helping you secure your environment. The guide comes in the form of an Excel spreadsheet and offers 3 levels of security settings called Risk Profiles ranging from 1 (Ultra-sensitive environment – 3 digits agencies) to 3 (Everyone should implement them).
You can find the guide here. Once you download the guide, have a look at the different guidelines and define a Risk Profile to comply with. You may have to have a chat with your security officer. You can then look for the guidelines that don’t apply to your environment. For instance, you may not care that your ESXi host is not in AD and disregard this guideline when establishing compliance.
When you have defined the list of all the guidelines your environment must comply with, you need to verify what settings are configured in your environment. This is where vRops 6.7 comes in handy. The Security Compliance dashboard helps you monitor the level of security compliance of you environment. A great addition for you and your IT manager.
Enable SCG compliance
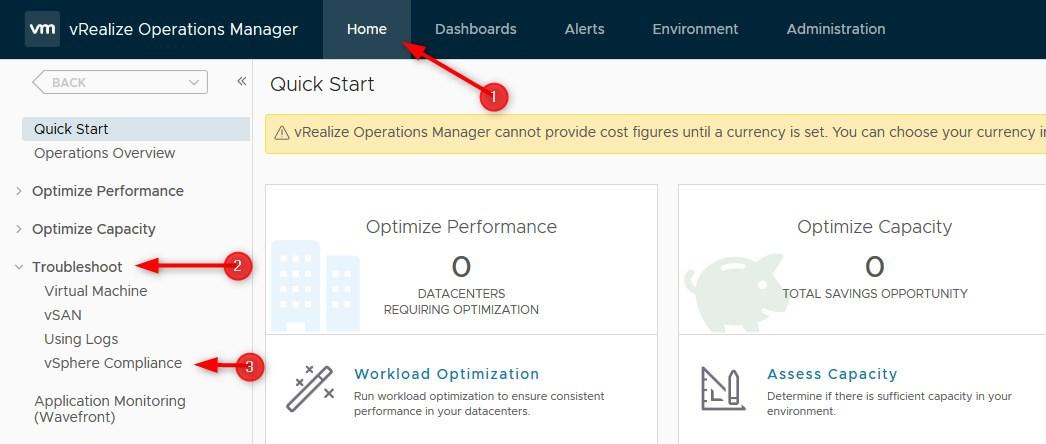
- First off start by logging in vRops as an administrator and browse to Home > Troubleshoot > vSphere Compliance
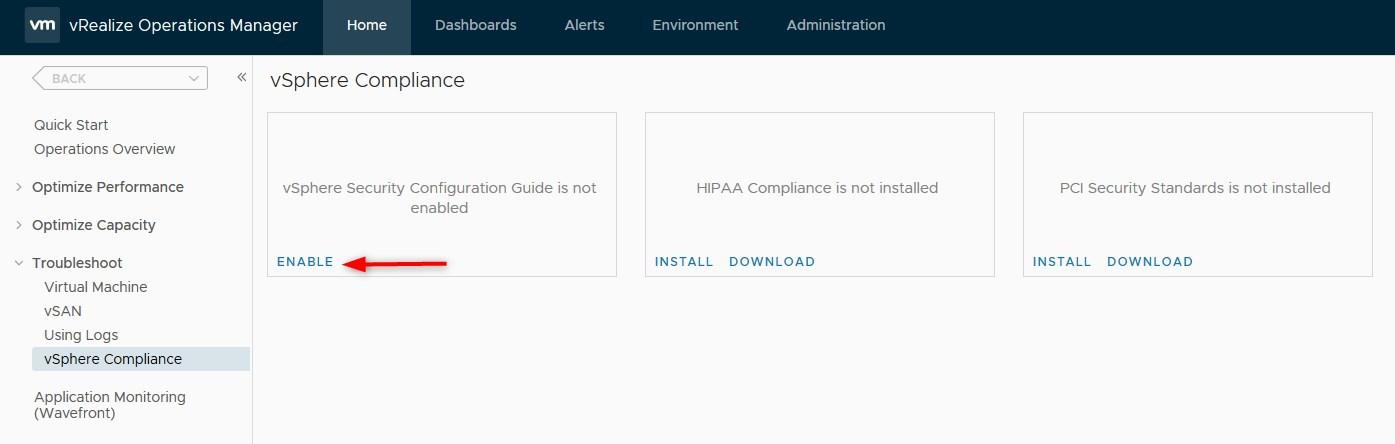
- Click on Enable to enable the Security Configuration Guide
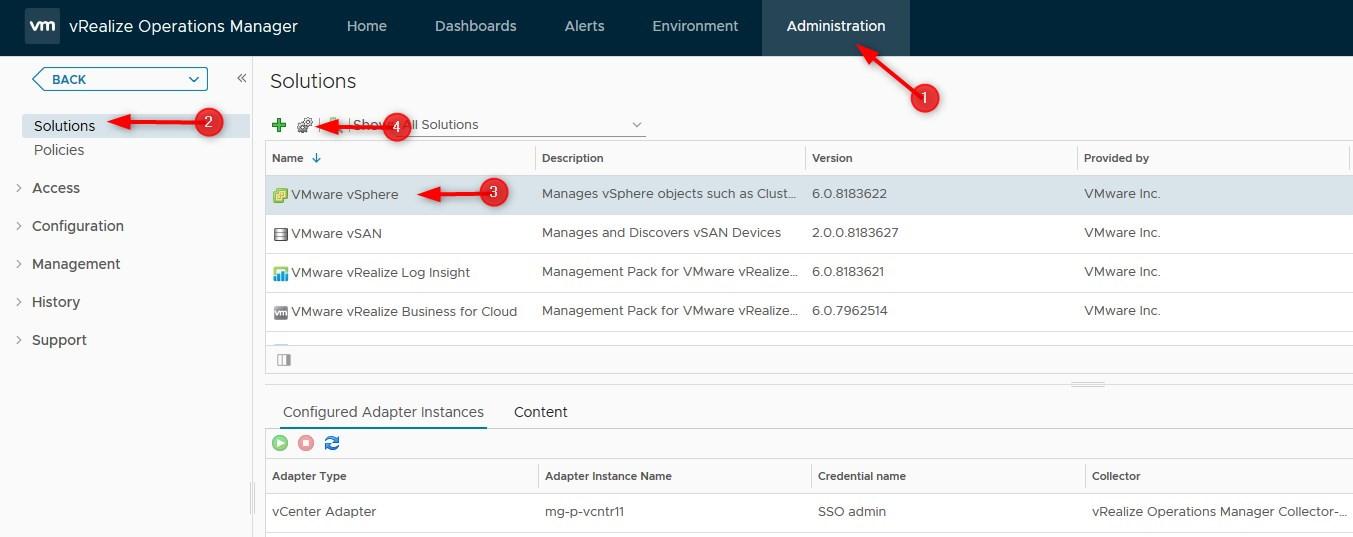
- Now we need to add it to the monitoring goals. Go to Administration > Solutions > Select VMware vSphere > Click the icon to edit its properties
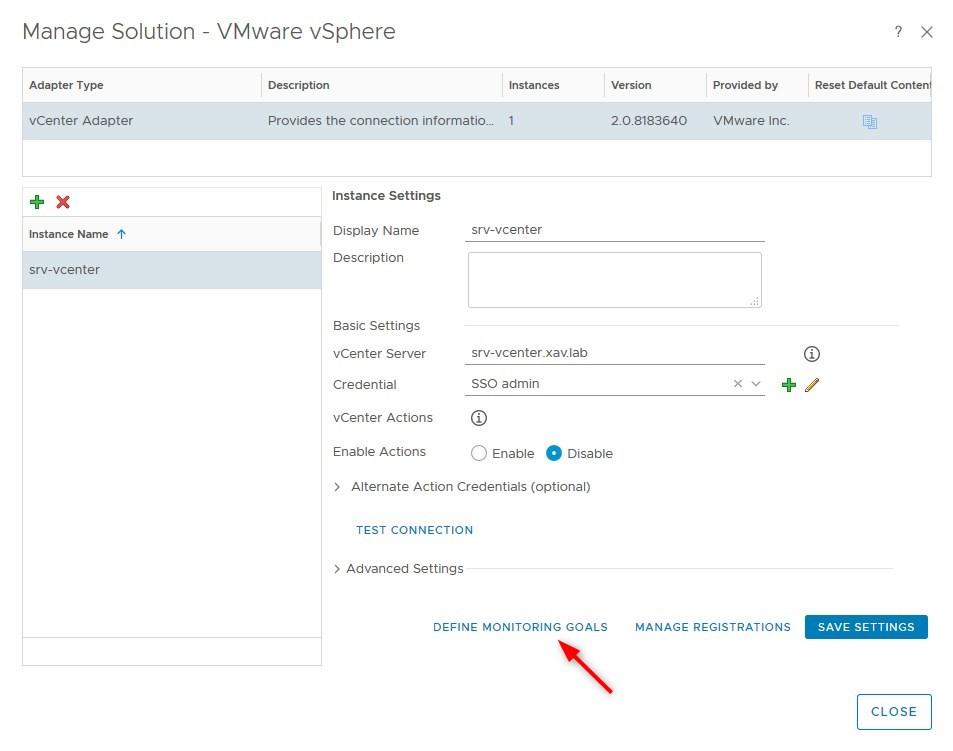
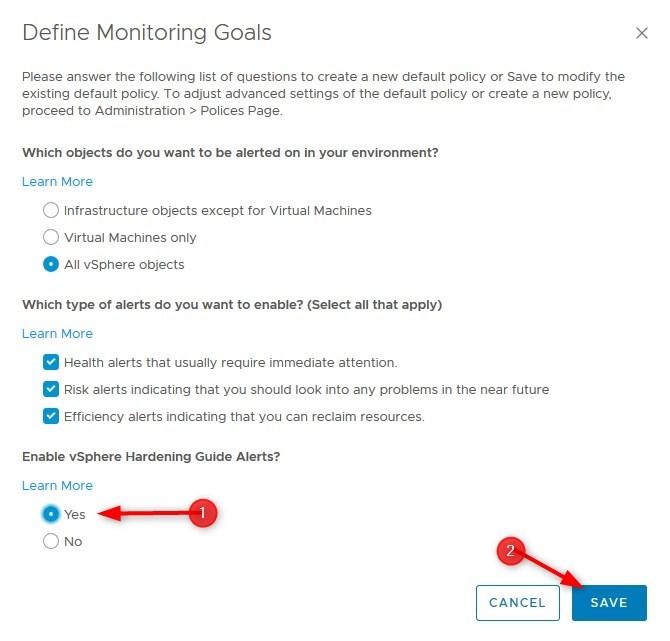
- Click on Define Monitoring goals
- Check Yes under Enable vSphere Hardening Guide Alerts and click Save
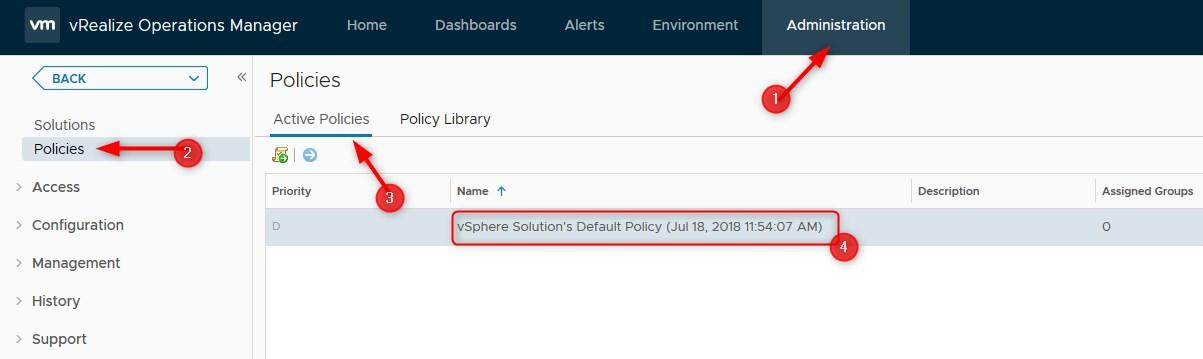
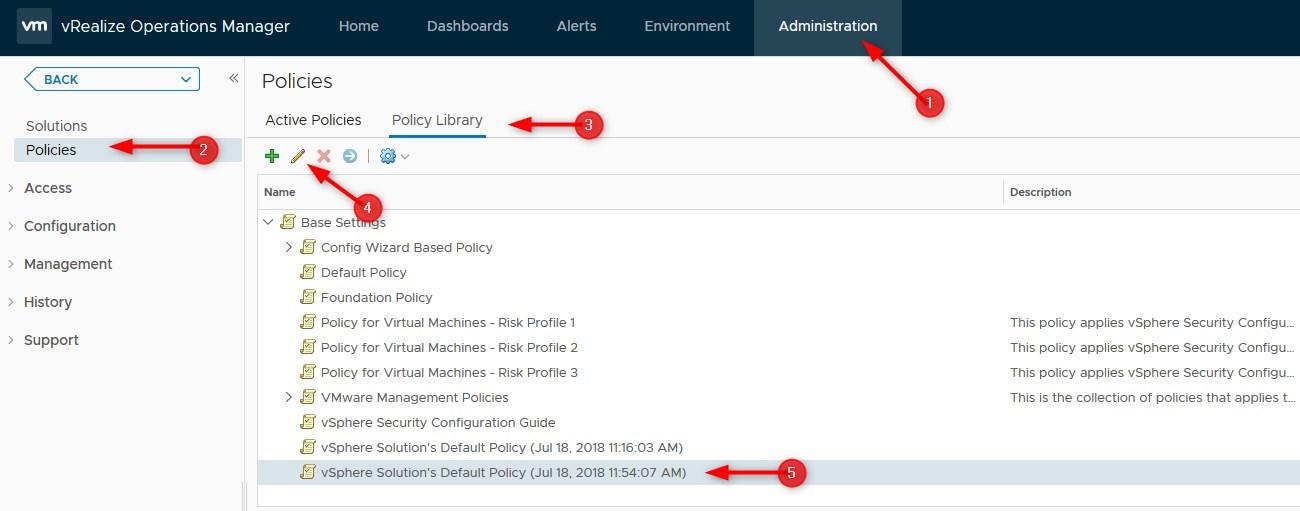
- Go to Administration > Policies > Active Policies. Take note of which policy is currently being used. In my case, it is the one from “11:54:07 AM”. It was created when we defined the monitoring goal
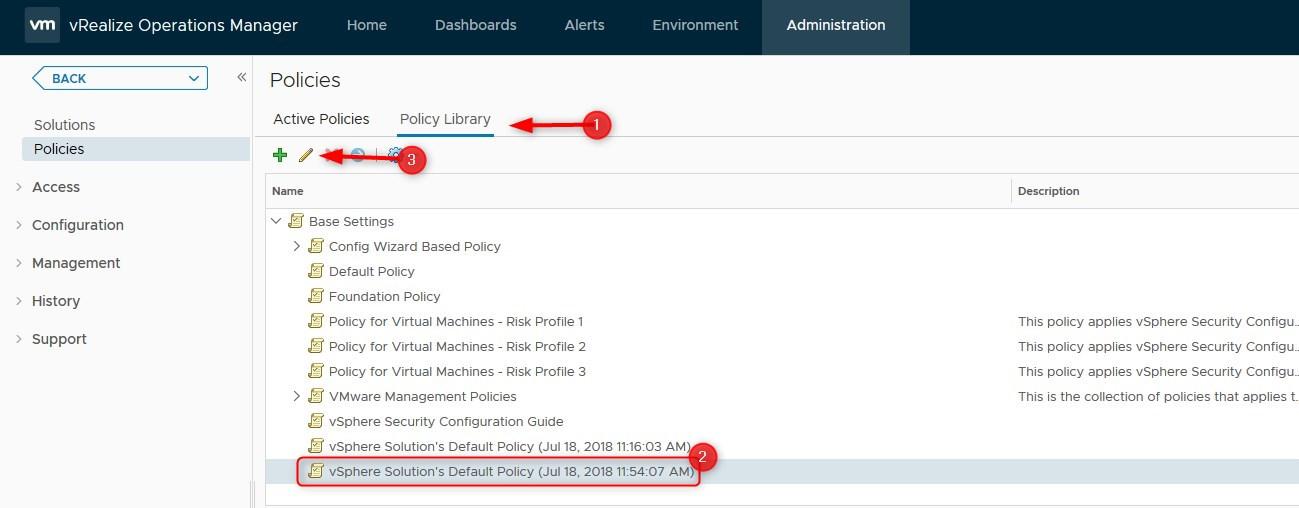
- Click on Policy Library, Select the active policy and click the edit button
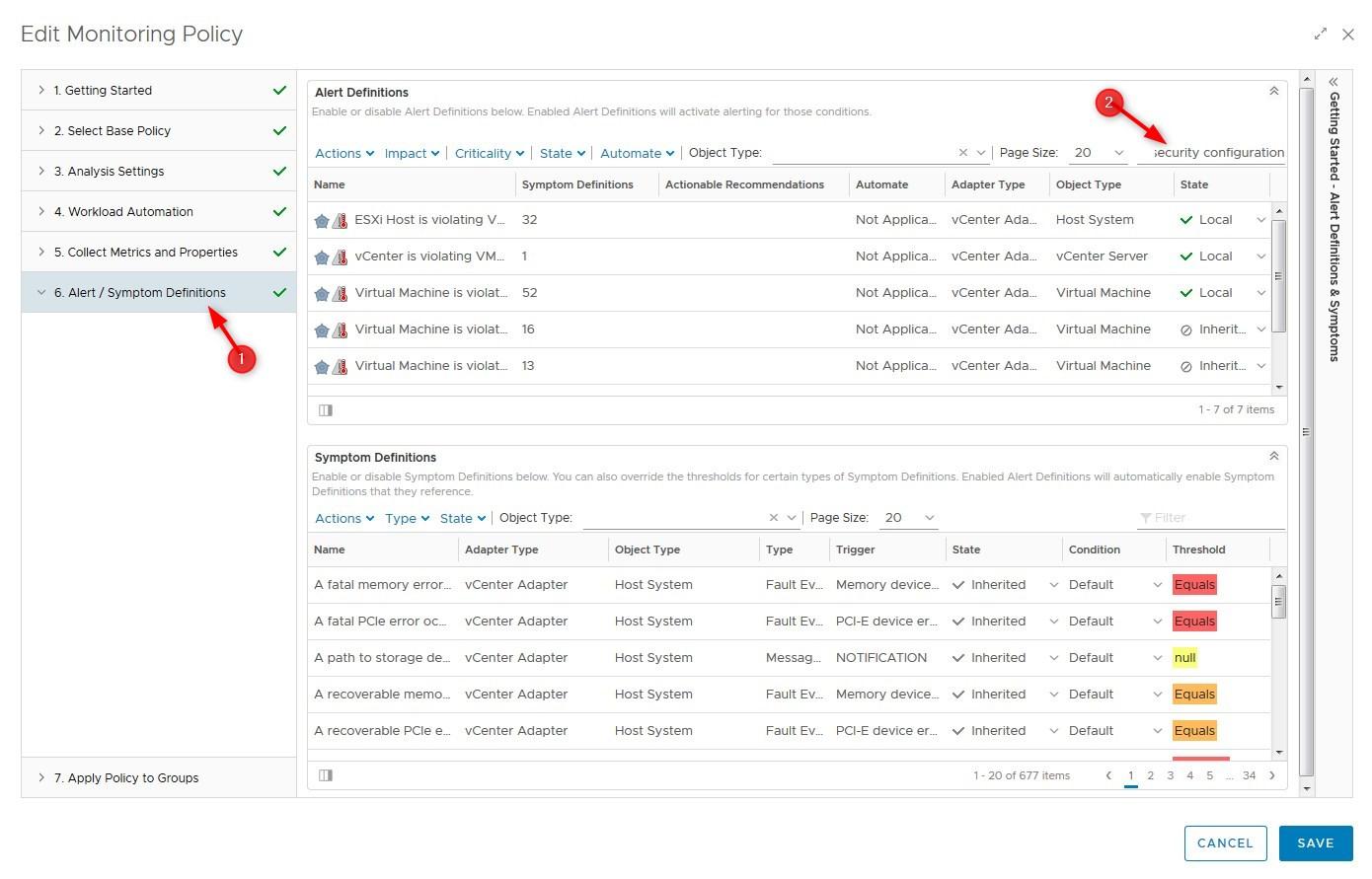
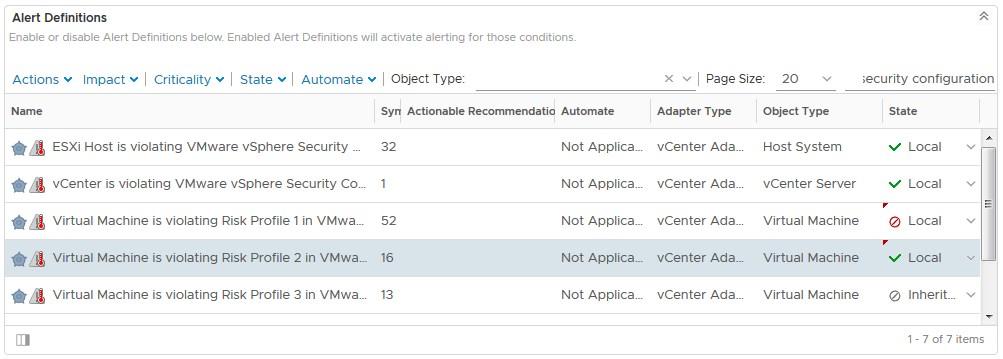
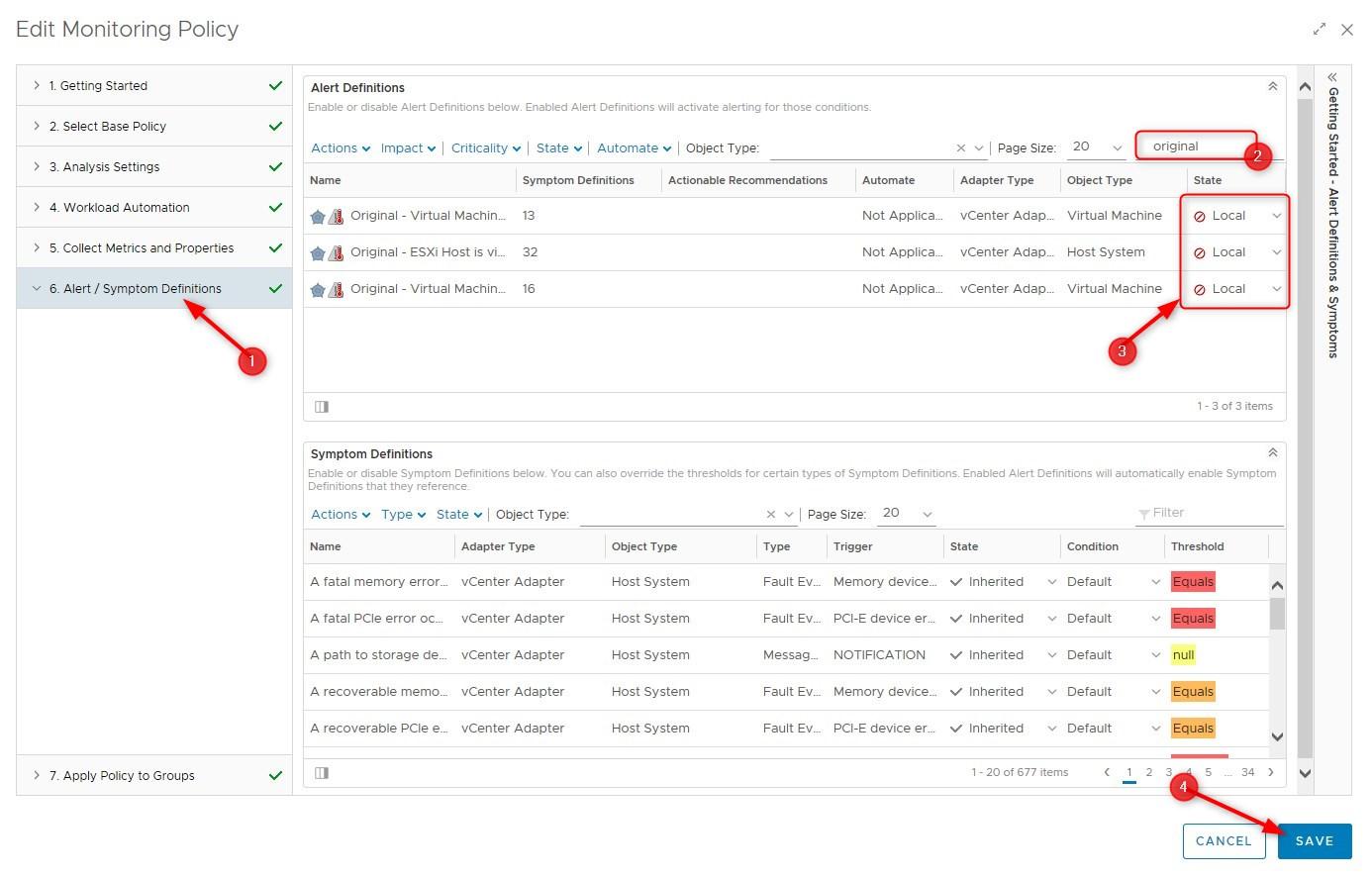
- Click on Alert / Symptoms Definitions > Type “Security Configuration” in the filter field and press Enter
- Only the SCG alerts are displayed. Select a Risk Profile for virtual machines by setting the more restrictive alerts to the state Local (disabled) and leave the less restrictive ones set to Inherit. In the example below I chose Risk Profile 2
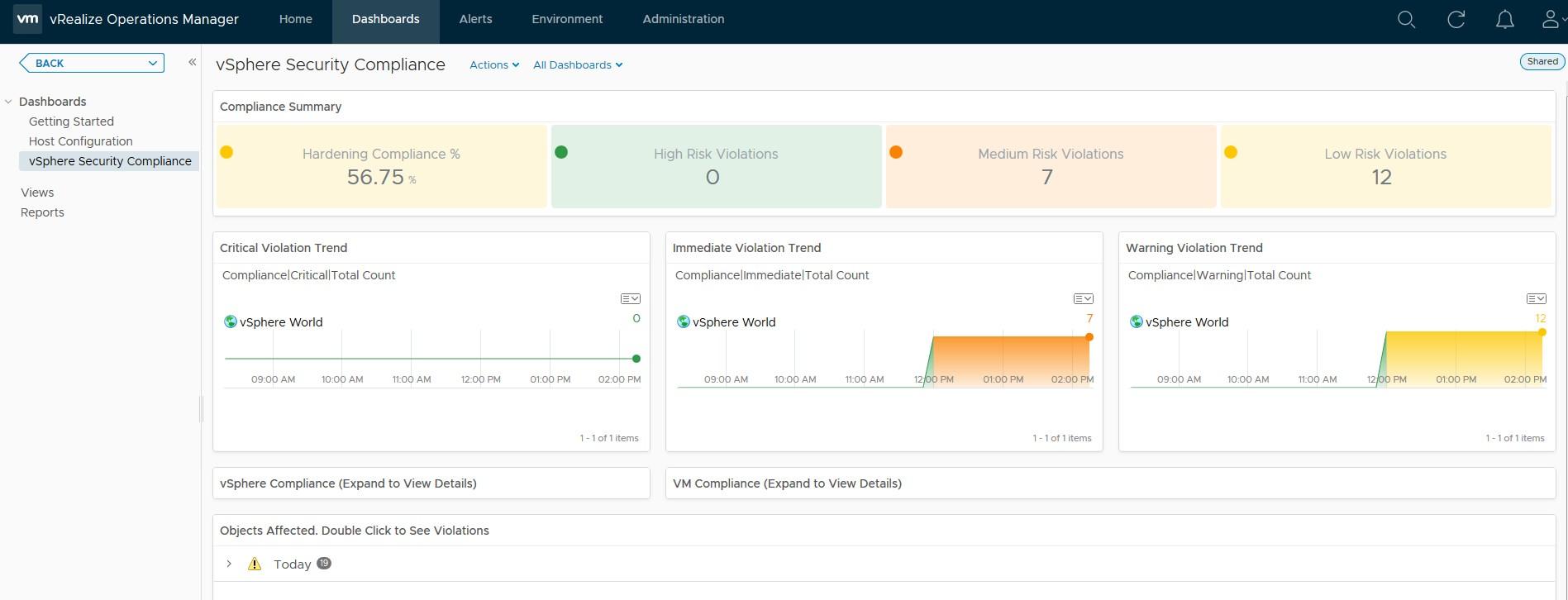
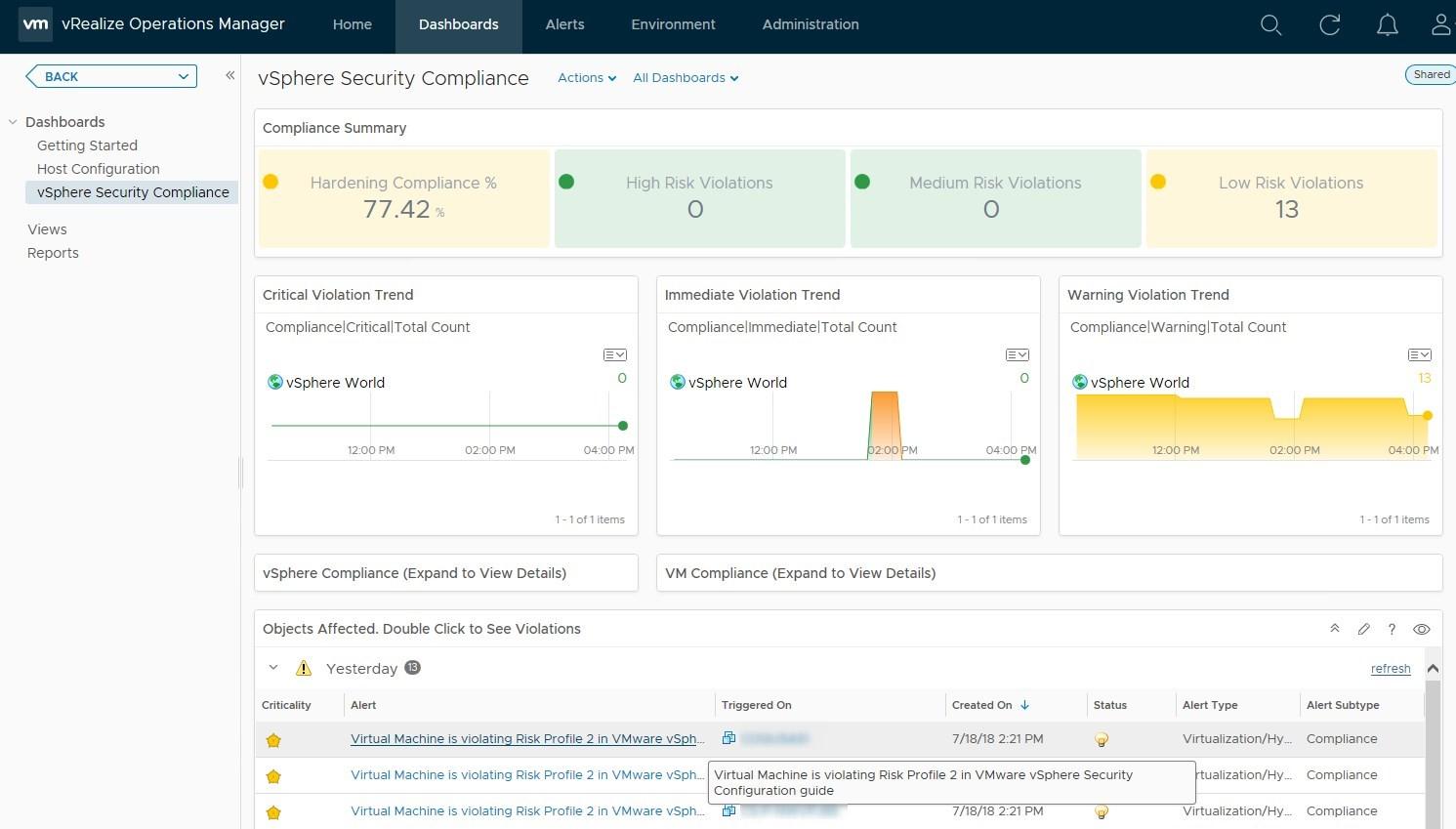
- You can now see the vSphere Security Compliance dashboard. It takes a few minutes to refresh after making changes so be patient. From here you can see how compliant you are and the different levels of risk where a guideline is violated based on the Symptom metrics
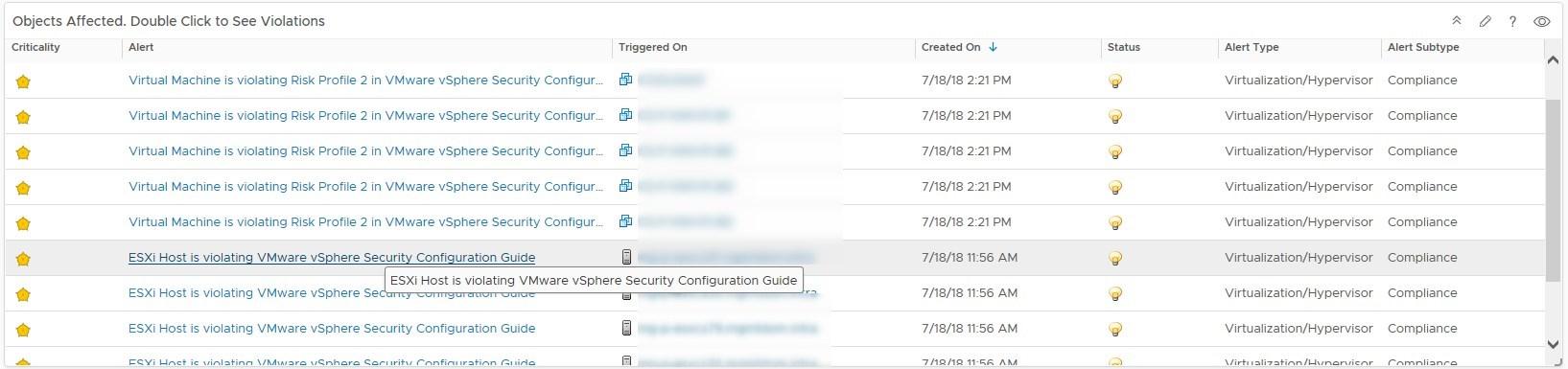
- At the bottom of the dashboard if you expand the view next to Today you will display the alerts per object. Let’s click on the alert of a host for the purpose of the example
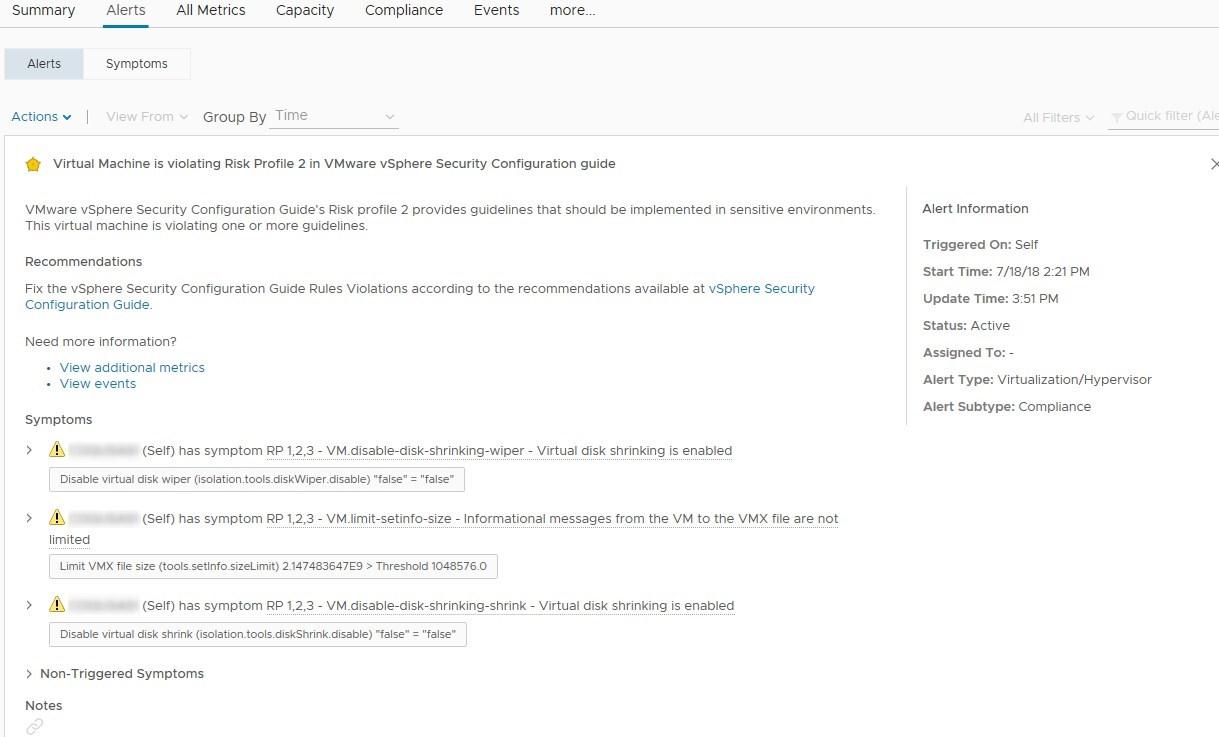
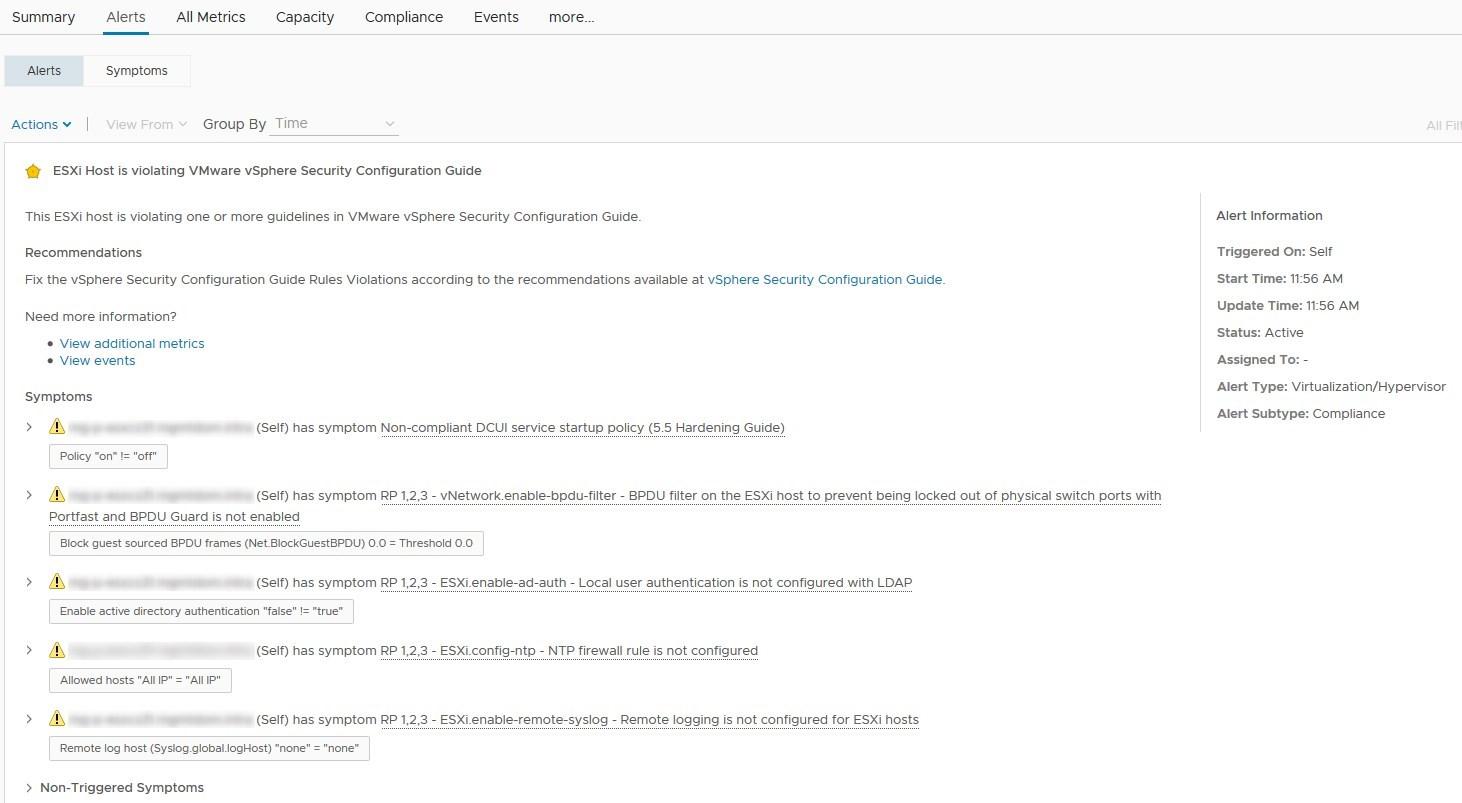
- We now see the Security Guide alerts. Out of these alerts, there are maybe a few that you don’t want to monitor. For instance, I don’t want to monitor Non-Compliant DCUI service startup policy because it was a part of the 5.5 hardening guide and disappeared in later versions. Though you may simply not want to monitor a given guideline because your internal security policies don’t require you to do it
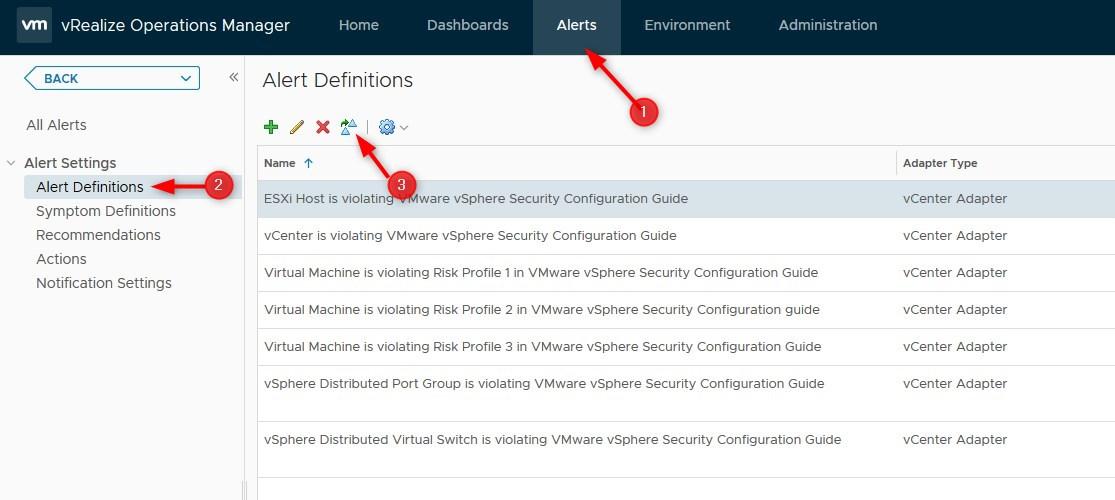
- To disable it, we need to remove the Symptom from the Alert Definition of the ESXi SGC. Go to Alerts > Alert Definition > Select the ESXi SCG alert and click the Clone button to save the default one
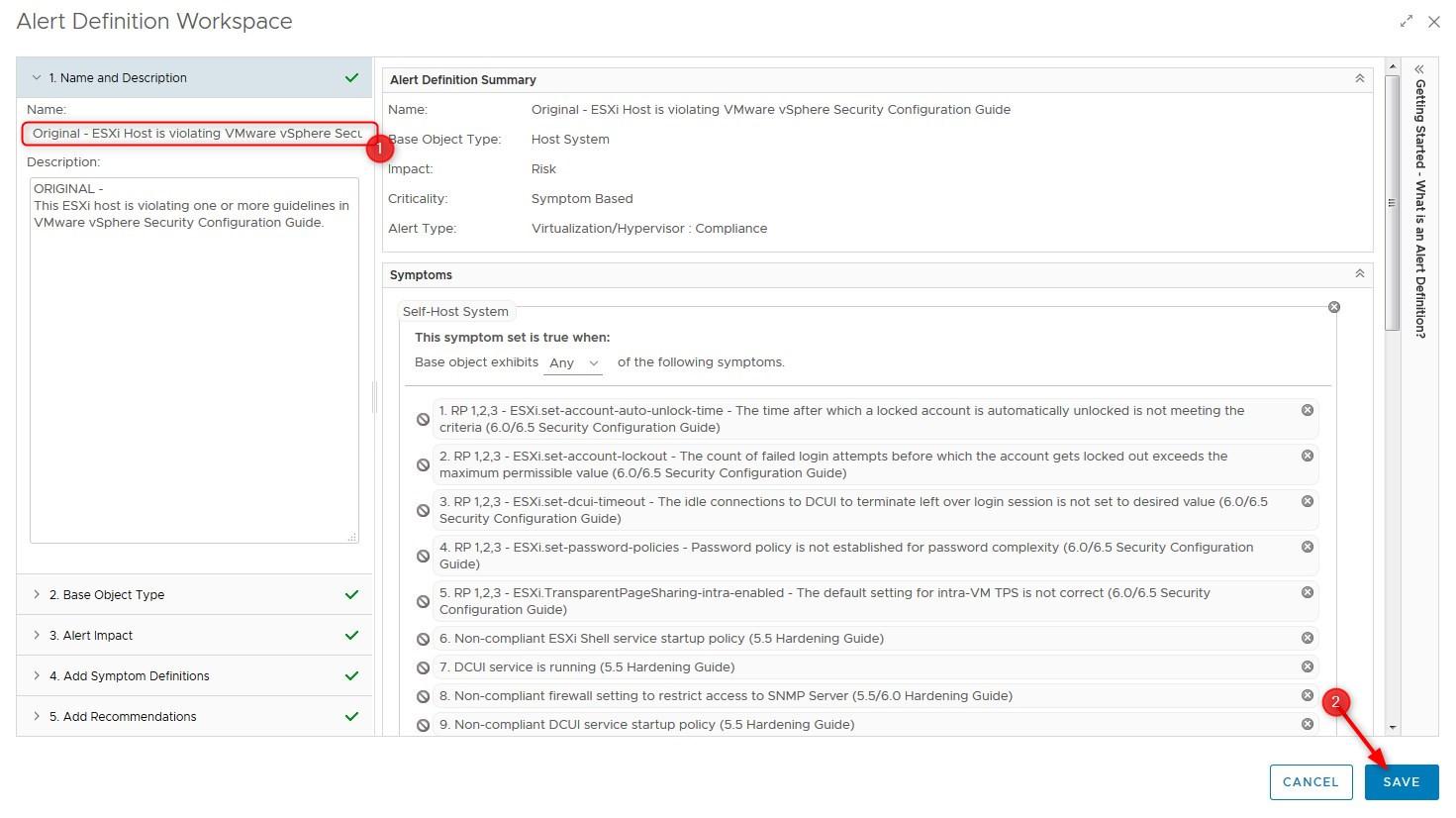
- Prepend Original – to its name and click Save
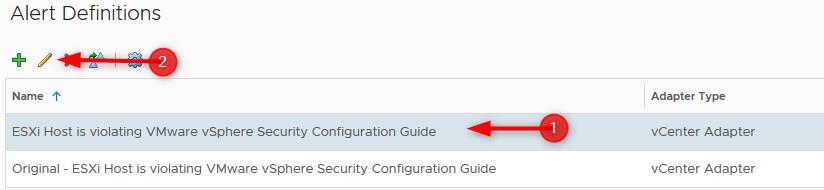
- Now Select the ESXi SCG alert again (not the clone), and click the Edit button
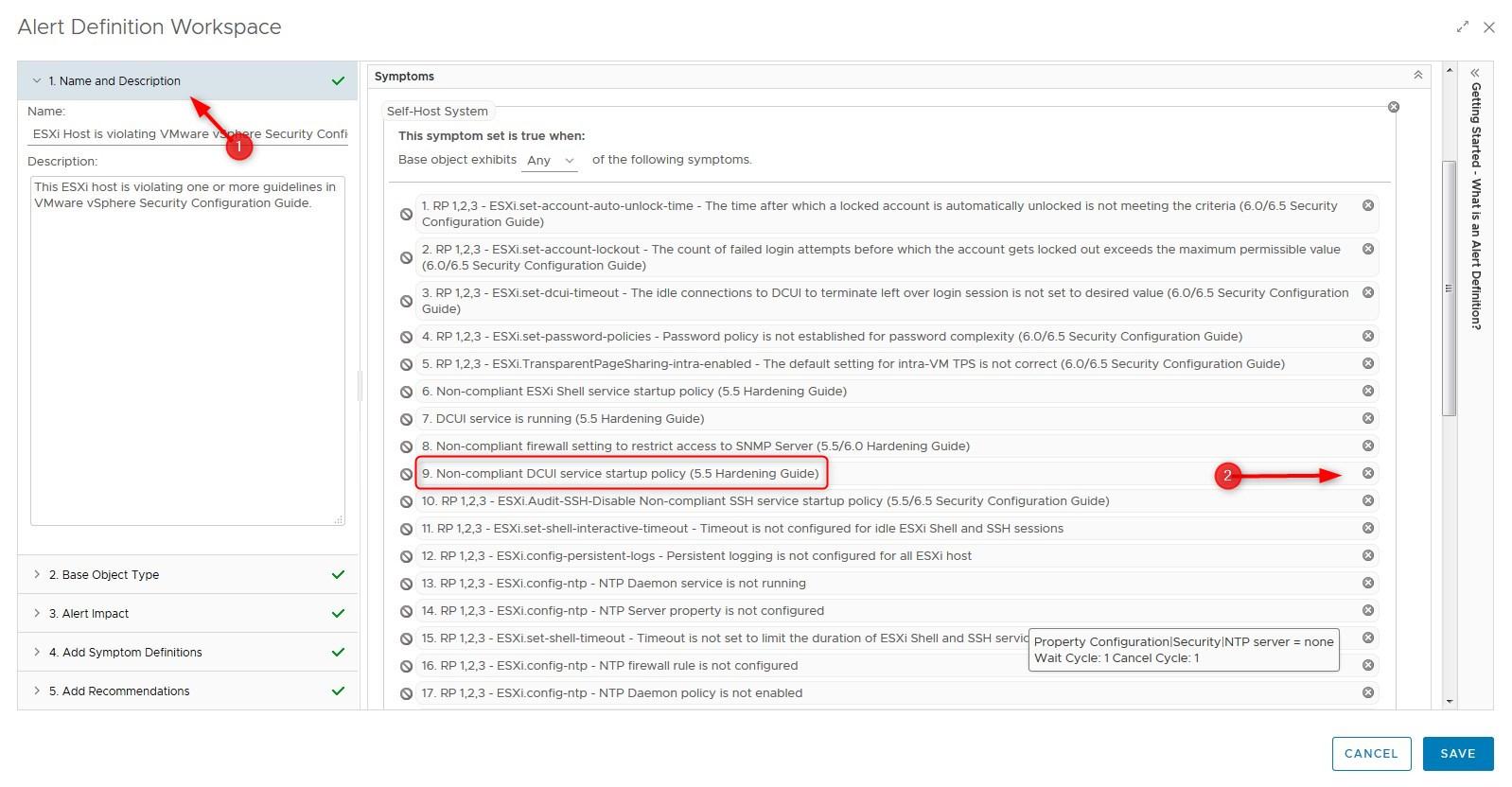
- Click on Name and Description > Find the Symptoms you want to remove and click the cross icon on the right then click Save. Apply the same method to the Virtual machine Risk Profile alerts (11 to 16)
- Click on Name and Description > Find the Symptoms you want to remove and click the cross icon on the right then click Save. Apply the same method to the Virtual machine Risk Profile alerts (11 to 16)
- Go back to Alert / Symptoms Definition > type Original in the filter field > Disable them all and click Save. You can see in the screenshot below that I also edited the alert definitions of virtual machine Risk profiles 1 and 2
- After a few moments, when the changes have been taken into account, you can display the Security Compliance display again that will only show the violated guidelines that you care about
- In my case, I have a few VM settings to add on my virtual machines for them to be compliant
Configure and tune the monitoring of SGC compliance
Now that the monitoring of the hardening guide is enabled, we are going to configure it to fit our needs by choosing a Risk Profile for VMs and disabling the checks that we don’t want to monitor (as discussed in the introduction).
Conclusion
The dashboard dedicated to the Security Configuration Guide is a really useful addition to an administrator’s tool belt, especially in a sensitive environment. It makes it a lot easier to report to higher-ups on the compliance of the environment to defined security guidelines and to quickly detect what is not compliant.



Very helpful and nicely explained, thanks